2
1
Here is my network topology, 101.101.101.101 and 202.202.202.202 are global IP while 10.0.1.1 and 10.0.1.251 are local IP. Host B is my computer. 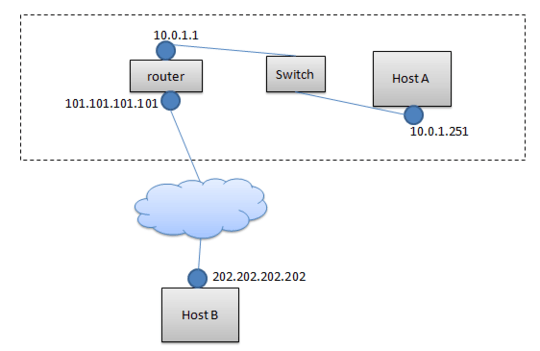
I can SSH to the router and then SSH to Host A on the router. Now I want to SSH to A directly by setting iptables on the router, such as: forwarding all the packets with destination host 101.101.101.101 and port 25122 to 10.0.1.251:22.
The follow three instructions are applied:
iptables -t nat -A PREROUTING -d 101.101.101.101 -p tcp -m tcp --dport 25122 -j DNAT --to-destination 10.0.1.251:22
iptables -t nat -A POSTROUTING -o br-lan -j SNAT --to-source 10.0.1.1
iptables -t nat -A POSTROUTING -o eth0.2 -j SNAT --to-source 101.101.101.101
After executed, they are shown in the list of iptables -t nat -v -n -L. The route rules on the router like this:
#route -n
Destination Gateway Genmask Flags Metric Ref Use Iface
0.0.0.0 101.101.101.254 0.0.0.0 UG 0 0 0 eth0.2
10.0.1.0 0.0.0.0 255.255.255.0 U 0 0 0 br-lan
After all these are done, however, I still can't SSH to A by "ssh 101.101.101.101 25122" on B. It just fails with:
Could not connect to '101.101.101.101' (port 25122): Connection failed.
The situation is, the tcpdump tools cann't be installed on the router to see the packects status there. But I can run tcpdump on Host A and confirm that no packet is forward from the router.
On the router,
#cat /proc/sys/net/ipv4/ip_forward 1
which shows the forward is enabled.
By running
iptables -t nat -v -n -Leach time after I did ssh on B, I can see the packets of PREROUTING of the router changes.Chain PREROUTING (policy ACCEPT 39526 packets, 3345K bytes) pkts bytes target prot opt in out source destination 14 712 DNAT tcp -- * * 0.0.0.0/0 115.156.132.118 tcp dpt:25122 to:10.0.1.251:22
The first number (14) increases each time I run the ssh to port 25122 on the host B. This indicates that the packets arrived at the router but not forwarded?
- I run
iptables -v -n -Land find that the default policy of FORWARD chain is DROP while the INPUT and OUTPUT chain are ACCEPT. I then set the FORWARD chain to accept by usingiptables --policy FORWARD ACCEPT. However, the ssh still fails as above.
So, here I am. Can this be a problem of the hard limit of the router, or wrong settings of the iptables. If it is the latter, how should I set it to achieve my goal?
Thank you very much for any clues.
First thank you for the the detail answer. But I think the two SNAT rules are also necessary because I must make sure that the packets forwarded to Host B will get back from the router: this is only true if the Host B has set the router as its default gate way, while B is in local network. Any way, I will try your advice days later. – Akr – 2017-07-20T10:59:56.963
No, not so as host B thinks that it is doing SSH with the router. Host B does not need to know the packets are forwarded between router and A – r0berts – 2017-07-20T22:35:41.197