22
4
Recently, in the last year or so, I have noticed that it seems more and more difficult to reach certain kinds of sites, especially those in non-favored nations like Iran or Russia.
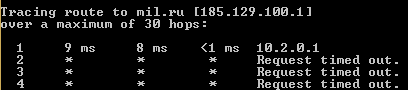
For example, just now I tried to reach the web site of the Russian Ministry of Defense (http://eng.mil.ru/en/index.htm), a site that I have legitimate business-related reasons for visiting, and it timed out. I tried the same site via a European proxy and had no problem connecting. I then tried a tracert and this was the result:
My interpretation of this is that the IP is being blocked by the company firewall. I asked our IT department what is the IP blocking policy for the network and was told that the policy is not determined by our company, but by the firewall service provider and that it is "secret and proprietary" to the provider and that they (meaning IT) had no control over that policy.
What is the story here? Are firewall product vendors just blanket blocking entire countries?
Just for giggles I decided to try different countries to see what would happen:
Finland ok
Poland ok
Russia blocked
Ukraine blocked
Estonia blocked
Turkey blocked
Saudi Arabia blocked
Afghanistan ok
Iraq blocked
Georgia ok
Armenia blocked
Uzbekistan ok
Alright, so I can visit web sites in Uzbekistan and Georgia, but not those in Armenia or the Ukraine? Who is making up this logic?
1What does a intrusion detection system have to do with content filtering? Your IT departments response is complete nonsense. A IDS and a firewall are not the samething – Ramhound – 2016-12-28T23:51:46.570
@Ramhound Ok, fill me in then, I am trying to understand why and how certain countries seem to be blocked and others are not. – Tyler Durden – 2016-12-28T23:59:46.767
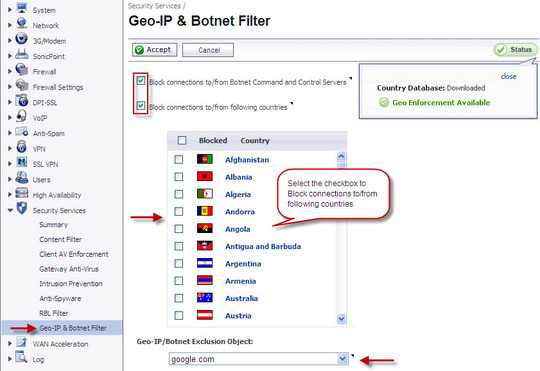
Sounds like your company uses content filtering and top of something like a SonicWall and how it works would be proprietary – Ramhound – 2016-12-28T23:59:55.043
Most content filtering systems can block content by country of origin. The specific reason you can't entirely depends how the configuration your company uses – Ramhound – 2016-12-29T00:04:28.100
7This is all really arbitrary and based on idiosyncratic needs. But I will say this: I work in the U.S. and have done work for U.S. companies whose web properties have utterly no value to anyone outside of the U.S. and it’s commonly been requested that some server-level filtering happens to block whole countries and IP ranges not because of censorship, but rather pragmatic needs based on the fact that their site would be consistently probed—and often have malware infections on them—that can be traced to specific countries or IP ranges. So this is really the state of the modern Internet world. – JakeGould – 2016-12-29T02:16:45.953
2I've implemented regional blocking myself using selective blackholing in order to mitigate the effect of DDoS flooding when I knew for sure that the vast majority of the customer base was geographically limited anyways. Very effective but probably won't help if you draw the wrath of something like mirai – Dmitri DB – 2016-12-29T03:36:33.347
That said most malware attacks tend to come from China or USA - which makes this method much less effective if you're within those two zones https://www.reddit.com/r/sysadmin/comments/3sadc9/those_of_you_who_block_countries_which_ones_are/
– Dmitri DB – 2016-12-29T03:37:52.863https://www.statista.com/statistics/440582/ddos-attack-traffic-by-originating-country/ as with DDoS traffic – Dmitri DB – 2016-12-29T03:43:20.713
@DmitriDB It's not about where most attacks are from, it's about the ratio of illegitimate to legitimate traffic for a given country. If you are serving users primarily in the USA, that means you have a lot of traffic originating in the USA that you can't block. If you have zero users in Ukraine and are seeing many attacks coming from Ukraine (a very common scenario), then you have every reason to just block Ukraine entirely. – Todd Wilcox – 2016-12-29T04:36:17.187
Yes, my point was that these methods will not work if the attackers are determined enough to source all their attacks to your local region in order to bypass your regional blocking countermeasures - a very real possibility in a post-mirai world for DDoS, and always has been the case if you're looking to block malicious traffic such as targeted attacks using methods best left to a WAF or RASP (portscans, bruteforces, etc vs. modsecurity, fail2ban, or cloudflare/incapsula for example) – Dmitri DB – 2016-12-29T05:41:38.600
1It's a standard part of a layered defense plan to block like that. It obviously has limitations, but is part of a larger overall plan. Even going back to the late '90's when places I'd worked at only had 56k lease lines (or occasionally the super fast T-1!). You'd not be likely to see it for global companies of course, but has been standard for quite some time for smaller, regional type companies. – Brian Knoblauch – 2016-12-29T12:23:33.770
2It's rather interesting why there is Estonia in that list. – Display Name – 2016-12-29T16:04:43.260
I've had to block large regions of China from accessing my server in the past due to spamming. No, this is not an unusual practice. – bwDraco – 2016-12-29T18:50:26.873