If we're talking about a cisco router,
acl inbound at an interface would mean 'let the acl process the packets coming into the router through that interface' i:e; while packets enter the router through that interface, but not on packets that exit through that interface.
acl outbound at an interface means 'apply the acl to packets exiting out of the router through that interface, but not on incoming packets.
Consider the scenario :
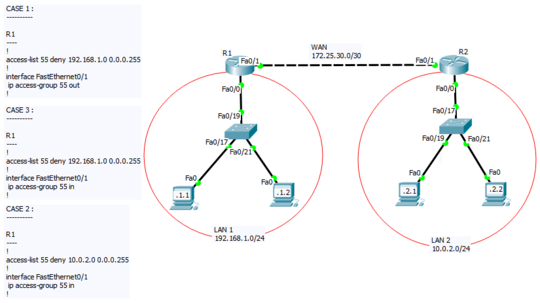
Ping from 192.168.1.1 to 10.0.2.1
When CASE 1 is configured :
The ping request will not pass through R1's Fa0/1, because acl 55 is set to process outbound traffic, and the source address of the request matches the IP range specified in acl. Ping output will be:
Destination Host Unreachable
When CASE 2 is configured :
The ping request will reach 10.0.2.1, but the reply from 10.0.2.1 will be stopped at R1's Fa0/1 because the acl is set to process inbound traffic and the source address of the reply matches the IP range in acl. Ping output will be:
Request timed out
When CASE 3 is configured :
The ping will be successfull. The ping request will not be filtered at R1's Fa0/1 as the acl is only for inbound traffic. Although the ping reply will be considered at R1's Fa0/1 as it is inbound, it will pass through because the source address of the reply is not in the 10.0.2.0 0.0.0.255 range, as specified in the acl.
