2
0
I have a headless home server running Ubuntu Server 12.04. A 3rd party website (to which I'm subscribed) periodically sends commands to a daemon on my home server which in turn responds to the 3rd party website. With static IP addressing, dynamic DNS client and port forwarding on the modem this is working as expected; All is good!
However, I now want to use OpenVPN client on my server to tunnel/route the server traffic through a 3rd party VPN server. I have successfully installed and configured OpenVPN client on my server but had found that while OpenVPN is running, the commands from the 3rd party website are either not being received by my server and/or my server is not acknowledging the command back to the 3rd party website. If I stop OpenVPN on my server it works again.
I suspect the problem is the 3rd party website sends the commands to my server (via the modem and port forwarding) but the reply is being routed over the VPN instead of back through eth0, where it came from.
The following diagram gives a basic overview of my home network.
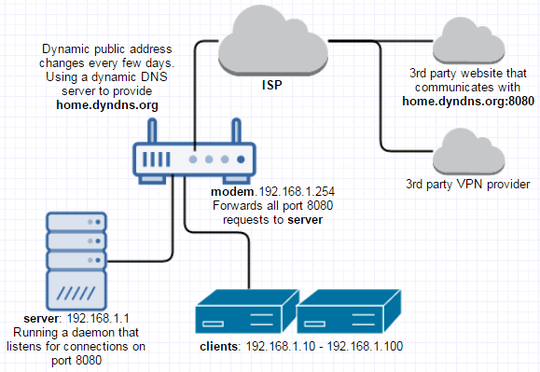
I'm not sure what further information is needed, but hopefully the following is enough to solve the problem.
Output of ifconfig with VPN active
$ ifconfig
eth0 Link encap:Ethernet HWaddr 00:07:e9:08:02:17
inet addr:192.168.1.1 Bcast:192.168.1.255 Mask:255.255.255.0
inet6 addr: fe80::207:e9ff:fe08:217/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:155309 errors:0 dropped:0 overruns:0 frame:0
TX packets:141790 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:211724221 (211.7 MB) TX bytes:20656517 (20.6 MB)
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
inet6 addr: ::1/128 Scope:Host
UP LOOPBACK RUNNING MTU:16436 Metric:1
RX packets:43 errors:0 dropped:0 overruns:0 frame:0
TX packets:43 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:2368 (2.3 KB) TX bytes:2368 (2.3 KB)
tun0 Link encap:UNSPEC HWaddr 00-00-00-00-00-00-00-00-00-00-00-00-00- 00-00-00
inet addr:10.167.1.6 P-t-P:10.167.1.5 Mask:255.255.255.255
UP POINTOPOINT RUNNING NOARP MULTICAST MTU:1500 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:2 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:100
RX bytes:0 (0.0 B) TX bytes:264 (264.0 B)
Output of route without OpenVPN running
$ route
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
default modem 0.0.0.0 UG 100 0 0 eth0
192.168.1.0 * 255.255.255.0 U 0 0 0 eth0
Output of route with OpenVPN running
$ route
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
default 10.111.1.5 128.0.0.0 UG 0 0 0 tun0
default modem 0.0.0.0 UG 100 0 0 eth0
10.111.1.1 10.111.1.5 255.255.255.255 UGH 0 0 0 tun0
10.111.1.5 * 255.255.255.255 UH 0 0 0 tun0
us-west.private modem 255.255.255.255 UGH 0 0 0 eth0
128.0.0.0 10.111.1.5 128.0.0.0 UG 0 0 0 tun0
192.168.1.0 * 255.255.255.0 U 0 0 0 eth0
I've found some other forums with similar sounding problems but have been unable to apply the information within to solve my specific problem.
http://www.overclock.net/t/1043127/solved-openvpn-client-blocks-inbound-ports
https://forum.linode.com/viewtopic.php?t=8737
Update: I've been told to investigate policy based routing which has led me to a similar question (Remote SSH access doesn't work when OpenVPN client is enabled on DD-WRT) but so far no answer there either.