It depends how random your password is.
If you choose a password from the following list:
"?e&ye&ga!ruaa!na!e%ta!e%rc#Iod$woH"2245aSBsb3ZlIHlvdSBLaXJzdGVuIFNoZWxieSBHdXllcg==
Then you have exactly 1 bit of entropy (it's either the first password, or the second).
That's when you read the XKCD comic that Dave linked.
But i can make some assumptions about your password:
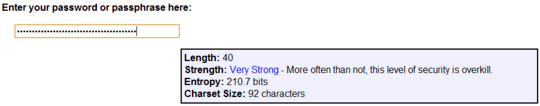
"?e&ye&ga!ruaa!na!e%ta!e%rc#Iod$woH"2245 (40 characters)
It looks like you use an alphabet of:
- uppercase
A-Z (26 glyphs)
- lowercase
a-z (26 glyphs)
- latin numerals
0-9 (10 glyphs)
- limited set of punctuation (assuming the 30 symbols on a 101-key keyboard)
That totals to an alphabet of 92 characters.
Further assuming that all your passwords are 40 characters, that gives you:
92^40 = 3.56+E78
or 3.5 quinvigintillion possible passwords.
To convert that into bits you do:
ln(92^40) / ln(2) = 260.94 bits
That's assuming your attacker would have to brute-force the password.
If we only want information, then the number of bits is actually much lower, because you actually used a much shorter alphabet:
original: "?e&ye&ga!ruaa!na!e%ta!e%rc#Iod$woH"2245
rearranged: aaaaacdeeeegnoorrtuwyHI2245""?&&!!!!%%#$
alphabet: acdegnortuwyHI245"?&!%#$ (24 characters)
Performing the same calculation:
ln(24^40) / ln(2) = 183.4 bits
Realistically there's fewer bits of information there because i can see that every time you type an e it is followed by a symbol:
So we replace e& with the symbol h, and e% with the symbol i:
original: "?hyhga!ruaa!na!ita!irc#Iod$woH"2245 (36 characters)
rearranged: aaaaacdghhiinoorrtuwyIH2245""?!!!!#$
alphabet: acdghinortuwyIH2245"?!#$ (24 characters)
Which reduces the information content to:
ln(24^36) / ln(2) = 165 bits
And i noticed that every ! is preceeded by an a and followed by a letter:
Replacing a! with k:
original: "?hyhgkruaknkitkirc#Iod$woH"2245 (32 characters)
alphabet: acdghiknortuwyIH2245"?#$ (24 characters)
Reducing bits to ln(24^32)/ln(2) = 146.7.
That only reduces the bits required for encoding, as we figure out the information content of the message.
These tricks don't help an attacker, who can't generally assume all passwords have these known sequences.
But there are some heuristics that can be programmed into a key search algorithm. People trying to type randomly type the same things a lot. For example i often get a collision when randomly typing:
adfadsfadsf
along with 18,400 other google results.
My most secure password is 57-characters, with a 27-character alphabet (a-z, 266 bits (ln(27^56) / ln(2) = 266.27).
On the other hand it is eleven words. There are about 2^11 common words in the english language. That gives:
(2^11)^11 = 2.66E36 passphrases => ln((2^11)^11)/ln(2) = 121 bits
Far less than the 266 bits that would be nievely assumed from random 57-character password.
i could add one bit if i chose between:
- spaces between the words
- nospacesbetweenthewords
Does the attacker know the general structure of the password, e.g. only ASCII characters, digits only at the end, all lowercase letters, and almost alternating letters and special characters? – Daniel Beck – 2011-04-09T08:42:50.183
not all lowercase ;) and no the attacker would not now the structure, it is based on a simple easy to remember sentence with some basic changes that are consistent. – abdadooo22 – 2011-04-09T09:16:16.763
See also http://security.stackexchange.com/questions/6499/best-password-strength-checker
– ripper234 – 2012-01-13T08:13:36.350Well now that you posted it here it is pretty easy to hack :). – Brad Patton – 2012-10-01T17:54:57.043