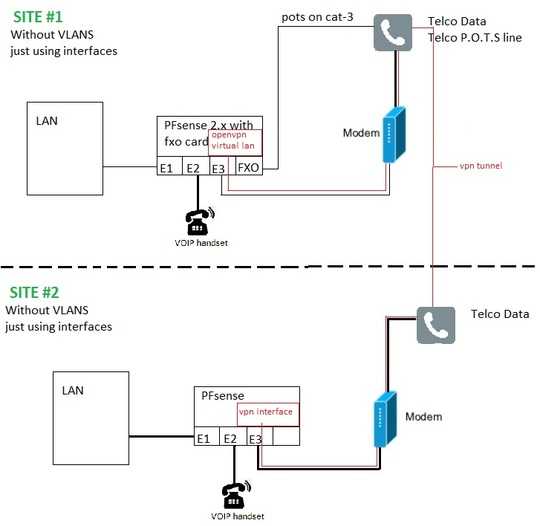
 I am writing these instructions with VLANS, as thats what is recommended for VOIP when building this from the ground up. Dont fret if you dont have this equipment, you can use physical interfaces in any instruction that mentions VLANS, just replace it with your interface name.
In my setup i used cisco SG-300 10p small business switches.
I am writing these instructions with VLANS, as thats what is recommended for VOIP when building this from the ground up. Dont fret if you dont have this equipment, you can use physical interfaces in any instruction that mentions VLANS, just replace it with your interface name.
In my setup i used cisco SG-300 10p small business switches.
There are a couple of reasons you'd want to use a switch in the way I am about to describe.
- It's a Gigabit POE switch, no need to deal with power bricks for the phones.
- Switches have ASIC hardware (Application specific intergrated hardware) and deal with traffic more effciently than pfsense will.
- Managed VLAN Capable switches allow you to fully utilize a single port on the Pfsense box (effective use of trunking allows you save on precious router ports for expansion later)
Let's get started. Assuming this is a fresh install of Pfsense 2.x (dont know if they ever brought the packages back to the newer versions) my installation is running 2.2.6
At this point you want to set up the interfaces, make sure its a Gigabit NIC
I used
"re0 vlan_10" for the WAN interface (setup for DHCP)
"re0 vlan_20" for the VOICE interface = 10.10.20.1 /24
"re0 vlan_30" for the LAN interface = 10.10.10.1 /24 (DHCP pool)
"re0 vlan_40" for the WLAN interface = 10.10.40.1 /24
"re0 vlan_50" for the CAM interface = 10.10.50.1 /24
On the switch create a 802.1q trunk port and tag it with vlans 10,20,30,40,50. connect the port you just configured to the port you just setup in pfsense. (if you are just using interfaces skip this step)
Additionally, map a port to vlan 10 untagged and connect this to the ISP modem.
Map one of the switch ports to vlan 30 untagged. Connect it to a computer, you should receive DHCP from pfsense and be able to reach the web managment interface on 10.10.10.1. Follow the inital wizard to complete setup. (connect to LAN Port if just using interfaces)
set-up DHCP pools for the VLANS/Interfaces the require it under Services > DHCP Server
At the first location you are going to want to run the dynamic DNS service and connect it to something like "no-ip.com" this will give you a FQDN like (mydomain.noip.me). The reason you want to do this is because most ip numbers on the WAN side change. This service is a dameon that relinks yourdomain.noip.me to the new number when it changes. If you skip this step you will most likely have to travel to the client VPN location to put in whatever the new ip number is. (or make a WAN rule for remote management.)
Next install the asterisk package, its under System > Packages > Asterisk.
It can then be configured under status > asterisk > edit configuration
you need to bind it to your voice vlan/interface in gtalk.conf under the [general] section (dont leave it at 0.0.0.0 as it will listen for registrations on each interface by default including the wan connection) The full instructions for getting asterisks up and functional for this, would qualify as an additional question, follow the information below and feel free to submit any additional questions.
For phones, I used AASTRA 6739i's (I was given a box of them for free)
they work extremely well, I have also used csipsimple on android and that works well. You can pretty much use any sip soft client you prefer, I would avoid used cisco phones. The prices are tempting for used ones but it's nearly impossible to get it working outside of their intended software (cisco call manager).
This should get you basic calling between two extensions
http://go2linux.garron.me/asterisk-simple-configuration-how-to/
Here is a guide for using asterisk with FXO Cards.
This would be good question to ask in the Pfsense section. I do not have experience in configuring fxo cards in Pfsense, as I'm basically using google voice as a digital trunk.
(instructions will be dependant on the chosen card. Google is your friend.) ;)
http://www.onlamp.com/pub/a/onlamp/2004/01/22/asterisk2.html
configure OPENvpn server (site-1)
I used certificates in my setup, because I have roaming internet clients. So for my particular setup, I wanted to be able to revoke a devices certificate if it was lost or stolen. For a site to site you probably dont need to go crazy with the setup. Additionally the higher the encryption goes (in bit numbers) the more work the Pfsense box must process.
https://doc.pfsense.org/index.php/OpenVPN_Remote_Access_Server
Now would be a good time to configure QOS (Quality of service). Its under firewall > traffic shaper I used HSFC in my setup, which happens to be the most complicated of all available traffic shapers in PFsense. It can be very effective for VoIP on links that degrade quickly, such as 3G/4G, but it can be complex to configure and tweak for proper operation. Depending on your specific requirements you can deviate from my recommendations. If you have multiple services running on your network this is an extremely important step. Ideally you want service priority in this order.
For hfsc, the range is 0 to 7. The default is 1. Hfsc queues with a higher priority are preferred in the case of overload.
Network control / acknoledgments (highest)7
Voice-6
Video-5
Reserved-4
Web Traffic-3
Bulk Traffic-2 (FTP/TFTP etc)
P2P traffic-1 (lowest)
googling "Pfsense hfsc tutorial" is how I learned how to use it. This is also a nice reference,
https://doc.pfsense.org/index.php/Traffic_Shaping_Guide
Once you have traffic shaping setup, its time to apply it to the network traffic. You can expect to traverse your network. In the firewall rules start allowing or denying traffic. The order of the rules is important, they are checked by the firewall top down, so if a rule doesnt match, it go's to the next one and so on untill it reaches the bottom. I put my default LAN rules at the bottom and put it in the lowest queue. Essentially this means if someone is using a service that wasn't deliniated, it won't disrupt important network traffic. You can think of it as a last ditch effort/catch all to put unwanted traffic in the p2p queue.
Example of a rule created and applied to a queue, you apply it under the advanced section when making the rule.

you can test your qos queues by going to status, then queues. Make a test call and make sure its in the right queue. This can be tested this way with each type of traffic.
At this point you should have a functional VPN, functioning asterisk server with a pots incomming call directed to both extentions.
You may need to enable the jitter buffer function, and its recommended on varying latency WANs.
But you may not know if you need it until you set-up the second site. (simple function added to the extension)
@Gizzy, I will probably update this multiple times this next week, when i have time to dedicate to it.


Tim, thank you for the reply. I have no idea what Asterisk is, but I will certainly look into it. Would this package automatically forward the pots incoming call to the second location? – GizzyBear – 2018-02-14T19:45:51.877
Tim, I am very intrigued by this option. Making my own private VOIP system between two sites is exactly what I am trying to do. Another question: Do I have to use Google for this to work or is that just for an extra number? I hate Google as a company. My ordinary pots number is sufficient for my purposes. I have no need for multiple phone numbers. – GizzyBear – 2018-02-14T23:32:06.080
One site has a 4 port dedicated pfSense box that I bought directly from the pfSense people (yes twice as expensive as reinstalling over a cheaper netgear box, etc. but I wanted to support the open-source community financially). The other site I have not set up yet. I have an unused Asus router with OpenVPN that I might use. I also have unused older PC hardware that could make a dedicated pfSense box. If pfSense is required at both ends then I will do the latter, and would provide space for a telephony nic card. – GizzyBear – 2018-02-14T23:41:58.010
Would this method using Asterix take advantage of the OpenVPN connection? I require the vpn for secure connection between the two machines. They both serve as nvr's for security cameras. Would Asterix force me to open ports up that might pose a security risk for the VPN? – GizzyBear – 2018-02-14T23:48:12.050
Tim, thank you for the info. This sounds like the best route for me to go. I'll have to figure out what a jitter buffer is and why I need it. But I'm sure someone made a YouTube video on it. Thanks for replies. I will try to use your method over next few weeks and do some jitter buffer/tweaking stuff research. – GizzyBear – 2018-02-15T00:07:05.223
Much appreciated. One last tangential question if you might know ... when I am setting up my OpenVPN on both pfSense firewall boxes and their respective PC's behind them, can I set them both up at one location behind a single ISP. I ask to make setup easy. If I can tweak everything with both systems in front of me at the same time it would greatly facilitate debugging them. Then once up and running, transfer one system to the remote location. OpenVPN requires server and client for site-to-site I believe. A 100 mile drive to tweak a variable that may or may not work is undesireable. – GizzyBear – 2018-02-15T00:34:53.623
Fanstastic. I'll give feedback in a few weeks to let you know what happened. Right now I am waiting on some multiport nic cards for the cameras to arrive before I start the install. – GizzyBear – 2018-02-15T01:20:29.303
if you can, delete the comments when you get a chance. the mods discourage long convo's in the comments section. Let me know if you need further help. – Tim_Stewart – 2018-02-20T18:49:09.370