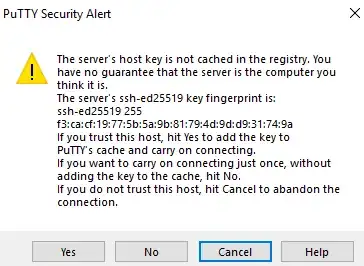
When I create a new EC2 instance running Ubuntu 18.04, using a new EC2-generated keypair, I convert the resulting .pem to .ppk using puttygen, then try to connect to the instance using PuTTY, and I am shown the expected prompt to confirm the SSH fingerprint:
PuTTY shows me a hex representation of an MD5 hash. This is the only fingerprint format PuTTY supports.
Outside PuTTY, the preferred fingerprint format these days is a SHA256 hash represented in Base64.
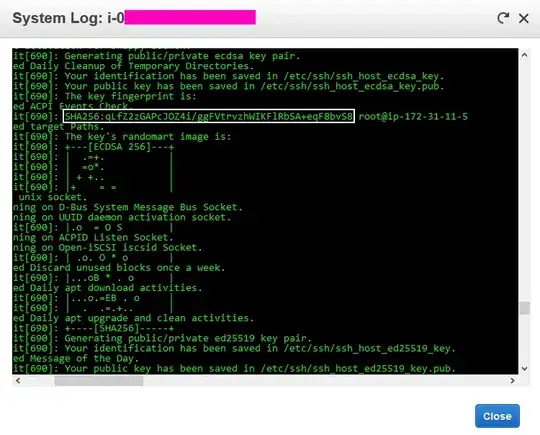
If I look in the EC2 system log of the freshly-created instance, sure enough I see the SSH fingerprints, SHA256 in Base64 representation:
Looking at this answer, Amazon Linux used to (perhaps still does?) output a hash in hex, rather than Base64.
How can I verify that the Base64 SHA256 fingerprint shown in the EC2 system log, matches up with what PuTTY is connecting to? I would rather avoid installing EC2-specific tooling.
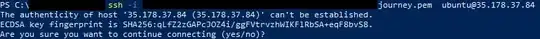
Incidentally, I had no trouble confirming the fingerprint when using OpenSSH from PowerShell. (I would consider using this rather than PuTTY, but it seems to lack mouse support.)
Also, I found this answer informative, but it doesn't give me an answer.
(All details shown in screenshots reflect a short-lived instance. I have destroyed the keypair.)