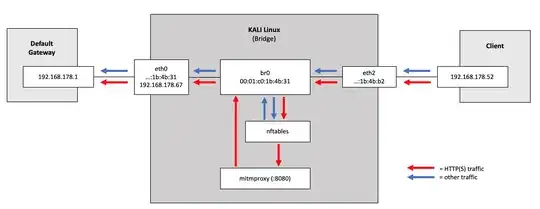
I have set up a bridge and would like to redirect HTTP/HTTPS traffic traversing it to a local port (8080) so that I can further process it using mitmproxy.
So far I was using a combination of ebtables & iptables rules. Unfortunately, I had to learn that eatables does not support the table 'broute' anymore and that I should use nftables instead.
Software used:
- KALI Linux 2019.4
- nftables v0.9.2
- mitmproxy v4.0.4
How I created the bridge:
root@kali:~# ip link add name br0 type bridge
root@kali:~# ip link set dev br0 up
root@kali:~# ip link set dev eth0 master br0
root@kali:~# ip link set dev eth2 master br0
My interfaces:
root@kali:~# ifconfig eth0
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.178.67 netmask 255.255.255.0 broadcast 192.168.178.255
ether 00:01:c0:1b:4b:31 txqueuelen 1000 (Ethernet)
root@kali:~# ifconfig eth2
eth2: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
ether 00:01:c0:1b:4b:b2 txqueuelen 1000 (Ethernet)
root@kali:~# ifconfig br0
br0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet6 fe80::e8c3:adff:fe19:f804 prefixlen 64 scopeid 0x20<link>
inet6 2003:e5:3f18:d100:201:c0ff:fe1b:4b31 prefixlen 64 scopeid 0x0<global>
ether 00:01:c0:1b:4b:31 txqueuelen 1000 (Ethernet)
My routing table:
root@kali:~# route
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
default fritz.box 0.0.0.0 UG 0 0 0 br0
192.168.178.0 0.0.0.0 255.255.255.0 U 0 0 0 br0
At first, I thought that my goal would be fairly easy to achieve. That said, it turned out that nftables does not (yet) support 'broute' either (see this post). Luckily a workaround was mentioned in the post, too.
Still, it took me quite some time to get it going. So I decided to document what I was doing. Please do not hesitate to comment or offer an even better solution.
Thank you!
Tobi