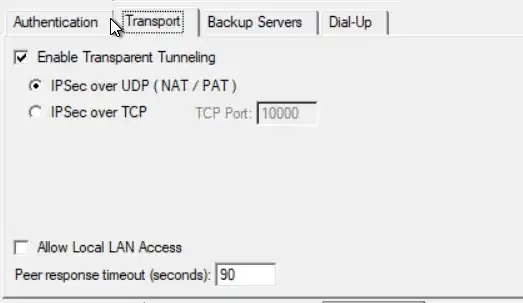
We're using an old version of this VPN client (stipulated by a client) to connect to their system. It looks like this:
I am running this on a VM accessed by RDP and the issue is as soon as I connect, my RDP session is lost and the VM cannot be seen on the local network.
I think this is a case for "split tunneling" but I know next to nothing about this. The only settings VPN client gives me are these, and I would appreciate knowing what they mean:
I only want/need this VPN connection to be used to let me RDP into their machines. So is it possible? And if so is it something I control, or something they control at sysadmin level?