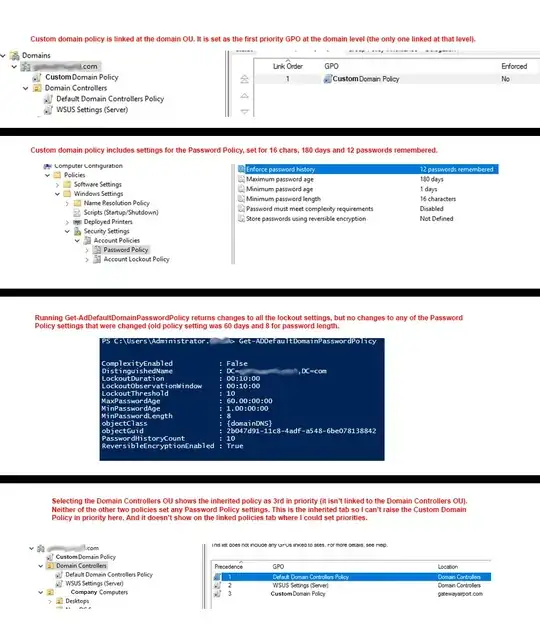
We are trying to modify our existing password policy that is being applied via GPO. For some reason it is not applying any of the settings in the password policy section (Comp Config > Policies > Windows settings > Security Settings > Account Policies > Password Policy).
We have password settings defined in only one of our GPOs. It is not the Default Domain Policy that was created on AD installation, we created a new policy and then modified this custom policy. The default domain policy is NOT linked, rather this custom domain policy is. Among other settings, the custom domain policy sets the password policies for the domain. We modified the custom policy recently to set MinPassowrdLength (MPL) to 16 characters and MaxPasswordAge (MPA) to 180 days. These settings under Password Policy are not being applied. If I change any of the Account Lockout Policy settings, they change just fine, just the Password Policy settings are not changing. I have tried changing the settings to see if they are being applied and then checking the default password policy (via PowerShell Get-ADDefaultDomainPasswordPolicy). I have tried the following (and I've tried to capture the results in the attached image):
- Making sure that this custom policy is the first in priority at the domain level in the tree (it's the only one listed).
- Adding a new policy and making it the highest priority at the domain level. I used different settings so that it would be apparent when I ran the PS cmdlt that I was looking at a different settings. This resulted in the Account Lockout settings changing, but NOT the Password Policy settings.
- Making the GPO that sets our password policy as "enabled" (right-click select enabled - locking it out) this forced it to the top of the priority lists on all downline OU's, but had some VERY unintended consequences so we made it NOT enabled.
- Ran Group Policy Results (in Group Policy Management) against the PDC and the results say the new settings should be applied to the DC.
- Linked the Default Domain Policy and set it in priority above the custom domain policy, again Lockout policies were applied, but not Password Policy settings.
I've been reading about having to make sure that the Password Policy applies to the domain controllers as the priority GPO, if I select the OU with our PDC/DC it is listed as first AFTER the GPOs applied directly to the OU. Neither of the two GPOs applied at this OU set password policy.
We are running Windows Server 2016 Domain Controllers with Active Directory at Windows Server 2012 R2 Domain and Functional Level.
I cannot see where I am going wrong, it seems that the settings that won't change were ones that we had previously set in the custom domain policy, but I'm apparently missing something somewhere to get this to work correctly. Any help would be appreciated.