I have a server with 2 WAN interfaces, eth1 and eth2. Each one have one router connected which gives them these IPs: 192.168.3.101 and 192.168.1.101.
The thing is that I want to completely avoid traffic through eth1 and instead create a tun0 which will tunnel all the traffic eth1 should receive.
I have complete control on which interface my programs should use (MPTCP will use all the interfaces it can that can reach the server), so I prepared a simple OpenVPN client/server configuration (binding to local 192.168.3.101), with server IP 192.168.99.1 and client IP 192.168.99.2. With this I have a working interface where I can send/receive data to 192.168.99.1 without problems.
Now the problem comes when I want to send/receive data to ifconfig.co (for example) using interface tun0. What I though it would do is to send data through eth1 to my server, then my server redirect the traffic to ifconfig.co, but that's not what is happening. It simply drops the connection:
If I try with interfaces eth1 and eth2 everything works as expected.
I've read/tried a lot of things for about 7 hours without stop and now I'm really lost. I'm not sure what is happening or what I'm doing wrong.
I think is a routing problem because when I try the command above tcpdump shows nothing on server. Zero packets received. This is what I have for now:

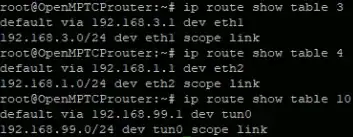
I see everything equal to each other, but eth0/eth1 are working and tun0 is not.
Just in case, this is my OpenVPN config (a simple point to point config):
;SERVER
dev tun
ifconfig 192.168.99.1 192.168.99.2
secret /etc/openvpn/static.key
keepalive 10 60
ping-timer-rem
persist-tun
persist-key
;CLIENT
dev tun
remote XXXXXXXXXXXX
resolv-retry infinite
local 192.168.3.101
lport 0
ifconfig 192.168.99.2 192.168.99.1
secret /etc/openvpn/static.key
keepalive 10 60
ping-timer-rem
persist-tun
persist-key
NOTE: I know that the convention for VPN IPs are 10.*, but I changed to 192.168.* as a desperate move to have a similar configuration as the other 2 interfaces.
The reason of all this is an idea to workaroud this issue: https://github.com/Ysurac/openmptcprouter/issues/670#issuecomment-533816813