I have created an nginx config that got a perfect score on Qualsys SSL Labs using only TLS v1.2, and I'd like to try and get a perfect score using both TLS v1.2 and v1.3.
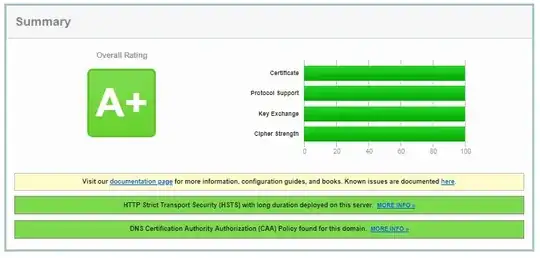
Consider this snippet of the version of the nginx.conf that is part of the A+ and 100% score:
ssl_protocols TLSv1.2;
ssl_ciphers AES256+EECDH:AES256+EDH:!aNULL;
It complains about a couple of the cipher suites, but it still gives an otherwise perfect score:
Now, if I add TLS v1.3 to the mix as the only config change, the score changes.
ssl_protocols TLSv1.2 TLSv1.3;
The cipher strength gets scored as a 90%:
I assume it's mad about those weak CBC ciphers:
TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 (0xc028) ECDH secp384r1 (eq. 7680 bits RSA) FS WEAK 256
TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (0xc014) ECDH secp384r1 (eq. 7680 bits RSA) FS WEAK 256
TLS_DHE_RSA_WITH_AES_256_CBC_SHA256 (0x6b) DH 4096 bits FS WEAK 256
TLS_DHE_RSA_WITH_AES_256_CBC_SHA (0x39) DH 4096 bits FS WEAK
There's not really a good way to remove the CBC mode ciphers perfectly, but maybe excluding SHA1, SHA256, and SHA384 will work. The config line becomes:
ssl_ciphers AES256+EECDH:AES256+EDH:!aNULL:!SHA1:!SHA256:!SHA384;
The cipher suite strength is still 90%.
It's no longer mad at the strength of the cipher suites:
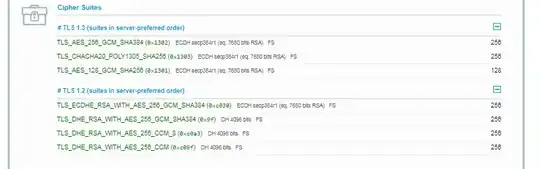
But apparently it's unhappy about the failing handshakes that worked before:
Which brings us to... the same cipher suites that are required for a successful handshake for older devices/apps are listed as "weak" and pass when only TLS 1.2 is enabled. Somehow enabling TLS 1.3 makes those same weak ciphers that pass before start failing.
It seems like the choice is: either enable TLS 1.2 only to get a perfect score, or, enable TLS 1.3 too but get dinged for the necessary cipher suites? It's a Kobayashi Maru of sorts.
Is it possible to get a perfect 100% score with nginx and TLS 1.2 and 1.3 enabled?