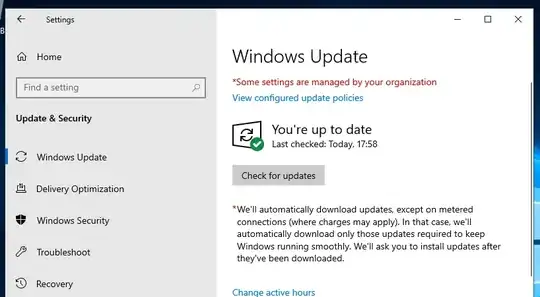
On a freshly-installed, non-domain-joined Windows Server 2019 (with desktop experience) VM, the ability to change Windows Update installation settings seems to have vanished, with the "Some settings are managed by your organization" message:
Viewing the configured update policies shows two set on the device, both with a type of Group Policy:
- Download the updates automatically and notify when they are ready to be installed
- Set automatic update options
However, running rsop and gpresult both (as expected) show no group policy objects applied. (It's a standalone system, so no domain policy applies.)
Is this expected?
Amazon also acknowledge this for their 2019 EC2 images, but it seems odd that using gpedit.msc is the only mechanism for enabling automatic update installation.