I have a problem with Universal groups across a trust - membership of the universal group gives rights from one domain in a forest but not from another domain in the same forest - I've set up a test set of accounts and groups to demonstrate and try and isolate and reduce the problem to the simplest I can.
I know this universal group across the trust can work - as on one of my domains the universal groups membership does work. In addition user membership within the domain and the across the trust also works. I need to isolate why the other domain in the same forest does not work.
I'm after some guidance of what I can look for - feel free to ask questions Thanks
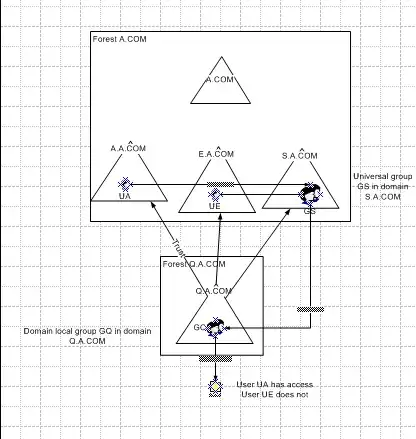
To explain (referring to the diagram )
I have two forests A.COM and Q.A.COM - The A.COM forest has four domains (A.COM, A.A.COM, E.A.COM and S.a.COM) and the Q.A.COM has one domain (Q.A.COM)
Q.A.COM trusts A.A.COM, E.A.COM and S.A.COM - These are one way non-transitive trusts - the only other trusts are the default trusts in the A.COM forest. All of these trusts are known to work and users in each of these domains can be added to groups in their own domain with membership in Q to get access to resources in Q.
I have the following users and groups setup in these domains
Name Type Domain Member/Right
UA User A.A.COM Member of GS
UE User E.A.COM Member of GS
GS Universal Group S.A.COM Member of GQ
GQ Domainlocal Group Q.A.COM Read rights to Folder
The User UA From domain A can access the folder but the User UE from domain E cannot.
If I use groups in domain A or E and add them to the GQ group then that works. This is our current workaround to the problem.
I have logged onto a memberserver of Q.A.COM and run WHOAMI groups for the user UA and it shows all the expected GS and GQ groups
For the user UE however neither the GS or GQ groups are shown. If run on a Q.A.COM member server then it does shown the GS universal group correctly.
So I believe its related to tickets or kerberos - and I have been reading about this and will continue, but I think I'm lost.
Finally other stuff I hav'e checked is as follows. Sites and services has been setup so that DCs from the two forest correctly locate the close DCs in the other forest
There is only a single non-GC server in each subdomain of the A.COM forest - this hosts the Infrastructure master role, so i think this means all DCs have all universal groups even the non-GC as it is the infrastructure master.
All servers in Q.A.COM are GCs - but this does not have the universal groups
We do have firewalls in many locations - but I see no denies on any of them during access.