Consider a Win 2008 SP2 machine with IIS7. The task is to apply a certificate and host name to the one and only Site on this machine. The site's host headers need to be abc.123.example.com
The first step was installing the .pfx to the Personal Store, which was successful.
IIS7 finds the cert as available, but won't allow the entry of a host name. The host name textbox is ALWAYS disabled/greyed out, even before selecting my cert. I've even deleted the default port 80 binding.
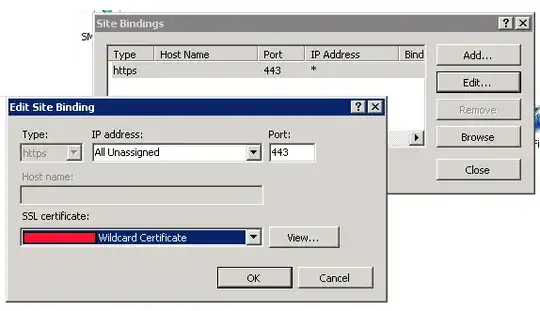
Question: how can I set a host name for this site? Is it a matter of this cert being a wildcard cert? I understand that the SSL request comes into the web server, and the host header in the packet is encrypted. Why then would IIS6 allow the host header to be specified, but IIS7 not?
Update: The cert isn't part of the problem. I've created a new Site on the machine, and when choosing https binding, the host name textbox is disabled.