Has anyone tried creating GPG keys for encrypted pillars on Ubuntu 18.04?
I'm using the following command to attempt to generate the keys:
gpg --gen-key --homedir /etc/salt/gpgkeys
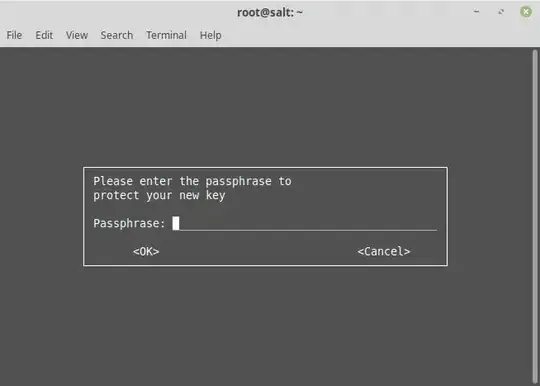
When I run that I get the usual set of questions, full name, email, etc. However when it gets to the passphrase screen, I seem to be unable to get past it without entering a passphrase. I get a ncurses display that looks like this:
If I just hit enter to get past it, it immediately pops right back up. If I hit "Cancel" then I get the following error:
gpg: agent_genkey failed: Operation cancelled
Key generation failed: Operation cancelled
Anyone run into this?