Thank you for your time, I incorrectly asked this in Network Engineering so I'm moving it here.
I have a Remote Office and a Main Office linked via IPSec with the Main Office being 192.168.16.0/24 and the Remote being 192.168.1.0/24. I can ping all devices in the Main Office from the Remote Office and vice versa.
Below is a simplification of what our network looks like:
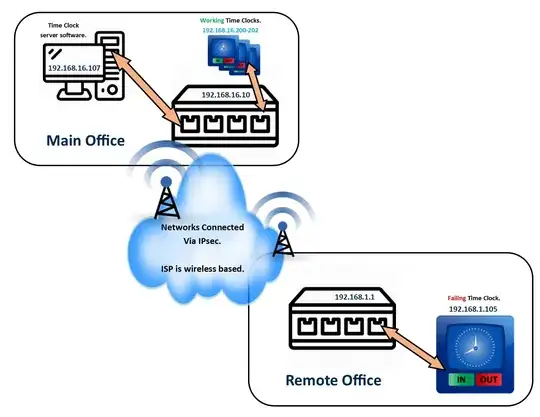
We are using TP-Link ER-6020 v2 routers with the latest firmware on both networks. Our ISP happens to use wireless connections as we are quite rural, though I don't think that really matters.
The Time Clock Server software is running on Windows Server 2012 (192.168.16.107) along with a few other applications. The Server Software can connect/discover Time Clocks on the 192.168.16.0/24 network with no problem but it cannot connect to the (192.168.1.105) Time Clock on the Remote Network even though it can be pinged. The Time Clocks use UDP 30303 and 30304 for communications. I have changed the Time Clock to eliminate a failing unit being the problem.
The Time Clock vendor has suggested that I set up some "Layer3 Management" rules or create some "Custom Routing Tables" but that seems to beyond my level of knowledge. Researching those has me thinking in circles with no end.
Please offer either a path towards solution or a Primer that might help me understand what the vendor is getting at so I can figure this out.