We're deploying Active Directory authentication policies and silos to restrict domain admins to domain controllers and server admins to servers which has worked fine on all of our servers from Hyper-V Server 2012 R2 to Windows Server 2016 (after executing klist -lh 0 -li 0x3e7 purge to force a refresh of the computer account's Kerberos ticket without rebooting) except for our 1 Windows Server 2008 R2 which fails with error:
Your account is configured to prevent you from using this computer. Please try another computer.
When this happens, the following event is logged on the domain controller:
Log Name: Microsoft-Windows-Authentication/AuthenticationPolicyFailures-DomainController
Source: Microsoft-Windows-Kerberos-Key-Distribution-Center
Date: 04/04/2019 09:25:50
Event ID: 105
Task Category: None
Level: Error
Keywords:
User: SYSTEM
Computer: <FQDN of DC #1>
Description:
A Kerberos Ticket-granting-ticket (TGT) was denied because the device does not meet the access control restrictions.
Account Information:
Account Name: <username of server admin>
Supplied Realm Name:
User ID: <down-level username of server admin>
Authentication Policy Information:
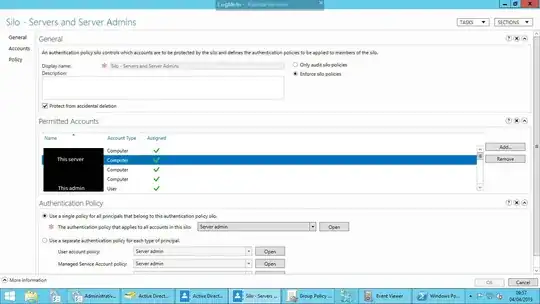
Silo Name: Silo - Servers and Server Admins
Policy Name: Server admin
TGT Lifetime: 120
Device Information:
Device Name:
Service Information:
Service Name: krbtgt/<NetBIOS domain name>
Service ID: S-1-5-21-<SID of domain>-0
Network Information:
Client Address: ::ffff:<IP address of server>
Client Port: 50847
Additional Information:
Ticket Options: 0x7B
Result Code: 0xC
Ticket Encryption Type: 0x7
Pre-Authentication Type: 0
Certificate Information:
Certificate Issuer Name:
Certificate Serial Number:
Certificate Thumbprint:
Certificate information is only provided if a certificate was used for pre-authentication.
Pre-authentication types, ticket options, encryption types and result codes are defined in RFC 4120.
https://docs.microsoft.com/en-us/windows/security/threat-protection/auditing/event-4768 says the following for the result code:
Code Code Name Description Possible causes
0xC KDC_ERR_POLICY Requested start time is later than end time This error is usually the result of logon restrictions in place on a user’s account. For example workstation restriction, smart card authentication requirement or logon time restriction.
So, for some reason, it thinks that the user account isn't allowed to access the server even though the server's computer account and and the server admin account are definitely added and assigned to the correct silo which can be seen below:
I've verified that the prerequisite of Kerberos client support for claims, compound authentication, and Kerberos armoring being enabled is applying via Group Policy:
Reboots haven't affected this.
The only thing that I can think of is that Windows Server 2008 R2 doesn't support authentication policies and silos which is backed up by the prerequisite policy Computer Configuration\Administrative Templates\System\Kerberos | Kerberos client support for claims, compound authentication, and Kerberos armoring not existing locally:
However, I haven't been able to find any documentation that explicitly says this. The closest thing to this is https://social.technet.microsoft.com/wiki/contents/articles/26945.authentication-policies-and-authentication-silos-restricting-domain-controller-access.aspx which says:
Prerequisites:
[...]
• Windows 8, Windows 8.1, Windows Server 2012, and Windows Server 2012 R2 domain members must be configured to support DAC, including Kerberos compound claims (device claims)
Even if this is the case, what's the workaround? A seperate group of admin accounts only for Windows servers pre-2012?