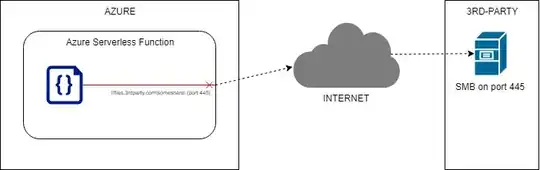
I have an Azure Function that needs to access an external SMB file share that is hosted on port 445. The Azure Web App sandbox that Functions run inside of explicitly blocks port 445. Assuming I have no control over the external SMB file server, what can I do to allow the Azure Function to access the SMB file share?
Some ideas... which ones are feasible?
- Setup an outgoing port-forward from a non-blocked port (say, port 555) to external port 445. Then have my Function app target the non-blocked port.
- Expose the file server via a "Virtual Network". According to the docs, the 445 port block rule is ignored if the target network interface belongs to the app. Can I add a 3rd party host as an interface on my app's virtual network? How?
- Is there a proxy service I can install and run in my Azure environment that can expose the file share on a different port?
How should I approach this problem?