I've created an extensive answer on Network Engineering regarding QoS, which is a copy/paste from there: https://networkengineering.stackexchange.com/questions/42660/implementing-cisco-qos-model-to-end-users/45176
The configuration might vary depending on equipment, but the commands are typically the same on any Cisco device. Answer two takes care of marking and prioritizing traffic based on the type of traffic.
Introduction
First off, let me write that i spend most of the summer trying to figure out a correct way to get this done. More so i had to hire a CCIE full time for a week or so to help out and in the process we had Cisco TAC trying to figure out an error on our 6500 series switches.
Why would you do this?
Today there's a virtual explosion of rich media applications on the IP network. This explosion of content and media types, both managed and un-managed, requires network architects to take a new look at their Quality of Service (QoS) designs.
The first step may seem obvious and superfluous, but in actuality it is crucial: clearly define the business objectives that your QoS policies are to enable. These may include any/all of the following:
- Guaranteeing voice quality meets enterprise standards.
- Ensuring a high Quality of Experience (QoE) for video.
- Increasing user productivity by increasing network response times for interactive applications.
- Managing applications that are "bandwidth hogs".
- Identifying and de-prioritizing consumer applications.
- Improving network availability.
- Hardening the network infrastructure.
With these goals in mind, network architects can clearly identify which applications are relevant to their business. Conversely, this experience will also make it apparent, which applications are not relevant towards achieving business objectives. Such applications could be consumer-oriented and/or entertainment-oriented applications. In the end it is all up to you.
The solution
I wanted to make this as easy and configuration free as possible. With that in mind combined with the fact, that QoS should always be processed in hardware, i was recommended to make use of the Auto-QoS feature in Cisco by the CCIE i hired.
So instead of marking traffic at the access level, the marking can be made by the end users or servers themselves. Auto-QoS then provides the correct classes for transportation of the traffic throughout the network. This enabled me to decide what applications or services which should be prioritized or de-prioritized via active directory group policies.
For starters i wanted to make it simpel. This meant prioritizing VoIP and Video applications, which is already predefined in Auto-QoS when you are using Cisco IP devices/TelePresence/Cameras etc., which we do.
Topology overview
We make use of the following access/core equipment.
- Core: Cisco 897 series, Cisco 3650 Series, Cisco 3850 Series and
Cisco 6500 Series
- Access: Cisco 3560CX Compact series and Cisco 2960X Series
Our topology is primarily based on a star topology, observe the following topology drawing (We use BGP in our WAN MPLS):
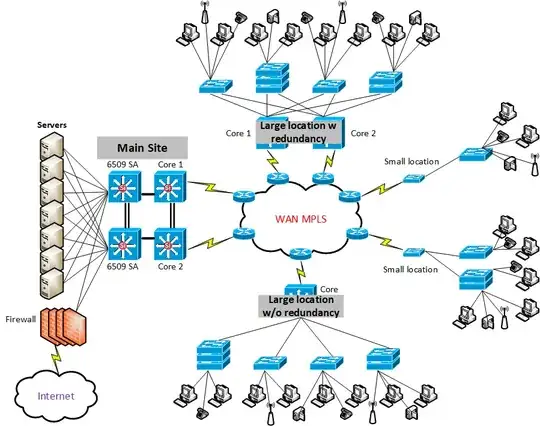
QoS on the access layer
The configuration is very simpel and straight forward, when using Auto-QoS. Remarking traffic and sending that to the MPLS ISP is a bit more complicated, but i will showcase examples below.
All access switches are setup with Auto-QoS, where all ports both access and trunk/uplinks are trusted with DSCP. Observe the following QoS table, where all values for DSCP, CoS, ToS etc. are setup in a table. This gives a good overview of the selected classes and the structure in which i'm trying to accomplish in my design:
Auto-QoS uses AF (Assured Forwarding) values for DSCP marking.
Enabling Auto-QoS on the access switch
Global configuration
mls qos (Activates QoS)
mls qos map cos-dscp 0 8 16 24 32 46 48 56 (Maps CoS to DSCP values, because CoS is a layer 2 marking, which cannot be routed)
auto qos srnd4 (Autogenerates all configuration in accordance to Cisco best practice SRND4 standard)
Port configuration
auto qos trust dscp (Activates QoS and trusts DSCP on a port)
priority-queue out (Sends all traffic to the priority queues)
That's it, the switch and ports will now run Auto-QoS.
Auto-QoS Configuration guide for the 2960X Series: https://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst2960x/software/15-0_2_EX/qos/configuration_guide/b_qos_152ex_2960-x_cg/b_qos_152ex_2960-x_cg_chapter_011.html
Enabling Auto-QoS on the Core layer
There's a big difference in the way QoS is handled by Core switches. The Cisco 6500 Series does not support Auto-QoS SRND4, therefore we will need to manually configure QoS and map it to the correct classes in order to preserve the Auto-QoS design. The Cisco 3650 and 3850 Series support Auto-QoS SRND4 and therefore it's pretty simpel to configure:
Enabling Auto-QoS on the 3650 and 3850 Series
Global configuration
auto qos srnd4 (Activates and autogenerates the QoS configuration)
Port configuration
auto qos trust dscp (Activates and autogenerates the QoS configuration)
When connecting the Core to the MPLS ISP, we want to remark the traffic into 5 classes (Because this is what our ISP supports). This is so, that the traffic will be prioritized through the MPLS to all the locations in the topology (See drawing for reference). Your ISP might be different and therefore the remarking should be made so it fits your design. The following example is how you remark all traffic into 5 classes.
You need to copy the auto generated Auto-QoS "AutoQos-4.0-Output-Policy" policy-map and then create a new one. You HAVE to use the same class-maps as generated by Auto-QoS. If you try to create your own they will be ignored, therefore the same class-maps are used and the marking is made from those classes:
policy-map WAN-OUTPUT-QoS (The name can be whatever you like)
class AutoQos-4.0-Output-Priority-Queue
set dscp ef
priority level 1 percent 10
class AutoQos-4.0-Output-Control-Mgmt-Queue
bandwidth remaining percent 10
queue-buffers ratio 10
set dscp af21
class AutoQos-4.0-Output-Multimedia-Conf-Queue
bandwidth remaining percent 10
queue-buffers ratio 10
set dscp af41
class AutoQos-4.0-Output-Trans-Data-Queue
bandwidth remaining percent 10
queue-buffers ratio 10
set dscp af21
class AutoQos-4.0-Output-Bulk-Data-Queue
bandwidth remaining percent 2
queue-buffers ratio 10
set dscp default
class AutoQos-4.0-Output-Scavenger-Queue
bandwidth remaining percent 1
queue-buffers ratio 10
set dscp cs1
class AutoQos-4.0-Output-Multimedia-Strm-Queue
bandwidth remaining percent 10
queue-buffers ratio 10
set dscp af41
class class-default
bandwidth remaining percent 25
The 5 classes will hereafter be prioritized and sent to the MPLS as follows:
- DSCP AF value: EF (VoIP)
- DSCP AF value: af41 (All Video media)
- DSCP AF value: af21 (Transactional data etc.)
- DSCP AF value: default (AF=0 & DSCP=0 Bulk data for instance)
- DSCP AF value: cs1 (Scavenger class For Bittorrent etc.)
The bandwidth percentages are used as remaining. This means that all classes are allowed to use 100% of the bandwidth and loan from the other classes if the bandwidth is not used. It's like bandwidth sharing, which means that whatever class is prioritized the highest will be able to send traffic if the link is congested.
The policy-map classes and percentages can be modified as needed to suit your individual requirements.
On the port uplink to the ISP the following needs to be configured:
interface XXX
auto qos trust dscp
service-policy input AutoQos-4.0-Trust-Dscp-Input-Policy
service-policy output WAN-OUTPUT-QoS
That's it for the 3650 and 3850 Series.
Enabling QoS on the 6500 Series
The 6500 Series does not support Auto-QoS SRND4. It's very basic and it only understands layer 2 CoS values for VoIP. This means you need to configure all QoS from the ground up, to fit the Auto-QoS infrastructure from the access layer. QoS needs to be configured based on which module is installed on the chassis. You also need to create policy-maps for both ingress and egress (input/output).
The Supervisor only understands CoS between the module and the ASIC in the chassis.
To activate Auto-QoS for CoS, you need to utilize the following global command:
auto qos default
This will create a table-map of CoS to DSCP, but the values do not all comply to the Auto-QoS SRND4 standard (CoS 7 is mapped to 54, which should be 56). Therefore you will need to remove the table-map and replace it with the following:
no table-map cos-discard-class-map
table-map cos-discard-class-map
map from 0 to 0
map from 1 to 8
map from 2 to 16
map from 3 to 24
map from 4 to 32
map from 5 to 46
map from 6 to 48
map from 7 to 56
To create QoS and policy-maps we need to find out, what queueing model a module is using. In the example below the Ingress and Egress queue is the same, but on some modules the Rx and Tx queues are different and therefore you will need to create policy-maps in accordance to how the queueing model is. To find out what queueing model an interface is using, you need to issue the following command. The below example is based on the module: C6800-16P10G
show queueing interface xxx | sec Transmit queues
Transmit queues [type = 1p7q4t]
show queueing interface xxx | sec Receive queues
Receive queues [type = 1p7q4t]
As written the queues are the same on this module and therefore we can use the same policy for both input and output.
1p7q4t basically means: 1 priority queue, 7 normal queues, where all 7 normal queues have 4 thresholds. You can get more info by searching for the module name and queueing. This module, the C6800-16P10G is explained in this link:
https://www.cisco.com/c/en/us/products/collateral/switches/catalyst-6800-series-switches/datasheet-c78-733662.html
See table 1, Queues.
Firstly we need to create the class-maps, that will be used for all policy-maps. This will match the DSCP values for the individual classes that matches the classes from Auto-QoS SRND4. Notice that the class-maps are created as lan-queueing with the match-all statement, which functions like AND/OR in programming. match-all=AND & match-any=OR.
Check the following configuration guide; Cisco Campus QoS design simplified, where configuration examples are provided per different modules at the bottom of the presentation:
http://honim.typepad.com/files/campus-qos-design-simplified-brkcrs-2501.pdf
225 pages, link is slow.
Creating class-maps (Global configuration):
class-map type lan-queuing match-all REALTIME-1P7Q4T
match dscp cs4 cs5 ef
class-map type lan-queuing match-all CONTROL-1P7Q4T
match dscp cs2 cs3 cs6 cs7
class-map type lan-queuing match-all MM_CONF-1P7Q4T
match dscp af41 af42 af43
class-map type lan-queuing match-all MM_STREAM-1P7Q4T
match dscp af31 af32 af33
class-map type lan-queuing match-all TRANS_DATA-1P7Q4T
match dscp af21 af22 af23
class-map type lan-queuing match-all BULK_DATA-1P7Q4T
match dscp af11 af12 af13
class-map type lan-queuing match-all SCAVENGER-1P7Q4T
match dscp cs1
You can change the names or edit as you like, to fit your needs.
After creating the class-maps i'll create the policy-map. It defines the priority of the DSCP value and sets the bandwidth in the different queues, after it matches a DSCP value.
policy-map type lan-queuing 1P7Q4T
class REALTIME-1P7Q4T
priority
class CONTROL-1P7Q4T
bandwidth remaining percent 10
class MM_CONF-1P7Q4T
bandwidth remaining percent 20
random-detect dscp-based
random-detect dscp af41 percent 80 100
random-detect dscp af42 percent 70 100
random-detect dscp af42 percent 60 100
class MM_STREAM-1P7Q4T
bandwidth remaining percent 15
random-detect dscp-based
random-detect dscp af31 percent 80 100
random-detect dscp af32 percent 70 100
random-detect dscp af33 percent 60 100
class TRANS_DATA-1P7Q4T
bandwidth remaining percent 15
random-detect dscp-based
random-detect dscp af21 percent 80 100
random-detect dscp af22 percent 70 100
random-detect dscp af23 percent 60 100
class BULK_DATA-1P7Q4T
bandwidth remaining percent 9
random-detect dscp-based
random-detect dscp af11 percent 80 100
random-detect dscp af12 percent 70 100
random-detect dscp af13 percent 60 100
class SCAVENGER-1P7Q4T
bandwidth remaining percent 1
class class-default
random-detect dscp-based
random-detect dscp default percent 80 100
After creating the policy-map you need to apply it to an interface:
interface xxx
service-policy type lan-queuing input 1P7Q4T
service-policy type lan-queuing output 1P7Q4T
To verify your configuration and to see that queueing is being performed you can use the following command (you might need to shut/no shut the interface for it to take effect):
show queueing interface xxx
To remark the traffic on the 6500 Series you need to create new class-maps and a new policy-map. The class-maps are not created as lan-queues and the match statement is match-any=OR instead of match-all as we want to check multiple values one after one. So if the first value does not match the packet, the next one will be checked and so forth.
I want to point out that this is where we had to involve Cisco TAC, because the following bug came up:
https://bst.cloudapps.cisco.com/bugsearch/bug/CSCuz52151
We had to change the class-maps from matching on AF values to raw DSCP values (discard-class) instead. We also had to upgrade the switch to version 152-1.SY5 (MD). After we followed these directions we've not had any problems since.
The configuration is as follows:
class-map match-any WAN-HIGH
match discard-class 32
match discard-class 40
match discard-class 46
class-map match-any WAN-GOLD
match discard-class 26
match discard-class 28
match discard-class 30
match discard-class 34
match discard-class 36
match discard-class 38
class-map match-any WAN-SILVER
match discard-class 16
match discard-class 18
match discard-class 20
match discard-class 22
match discard-class 24
match discard-class 48
match discard-class 56
class-map match-any WAN-BEST_EFFORT
match discard-class 0
match discard-class 10
match discard-class 12
match discard-class 14
class-map match-any WAN-SCAVENGER
match discard-class 8
After this we create the policy-map:
policy-map WAN-OUTPUT-QoS
class WAN-HIGH
set dscp ef
class WAN-GOLD
set dscp af41
class WAN-SILVER
set dscp af21
class WAN-BEST_EFFORT
set dscp default
class WAN-SCAVENGER
set dscp cs1
Then we need to apply it to an interface:
interface xxx
service-policy output WAN-OUTPUT-QoS
service-policy type lan-queuing input 1P7Q4T
That's it. I hope this information helps you. I understand when people say, that QoS is complicated. It can be done in various ways and the above example is just a snip of how it can be done. I know that Cisco are working on spreading the Auto-QoS SRND4 standard to more and more devices to help creating a good basis for Quality of Service.

