We have an ADFS 4.0 server with a WAP server set up in the DMZ. Recently, we started getting a HTTP Error 503: Service Unavailable error when accessing endpoints through the WAP. These same endpoints work correctly when accessing them on the network.
I have tried other endpoints and some work and some don't.
- Doesn't Work: https://server.domain.com/adfs/ls/idpinitiatedsignon.html
- Works: https://server.domain.com/adfs/portal/updatepassword/
I tried going back through the WAP configuration wizard and everything sets up correctly. I'm also not seeing any errors in the event viewer on either the ADFS server or the proxy server. Any ideas?
Update:
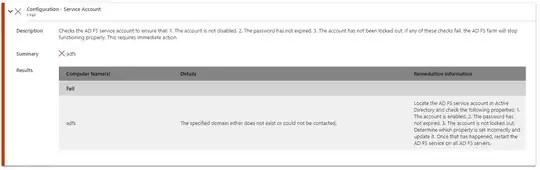
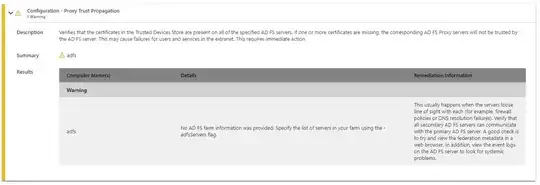
I've worked on this some more today. We ran the ADFS diagnostics tool and resolved all issues except for 1 error and 1 warning. I think the warning is just a tooling issue because the proxy server is able to see the federation metadata on the ADFS server. The error however has me stumped. I ran the ADFS Change User Account script and set it back to the gMSA user it's already set to and everything appeared to work correctly. I don't see how a gMSA account could be locked out, password changed or disabled. Everything appears to be set up correctly.