The following answer explains the files needed to prepare for ssh authentication using public-private key pairs ("Public Key Infrastructure" or "PKI"), and how those files are used during an actual ssh session. Some specifics here use names and directories that apply to linux, but the principles apply across all platforms, which use programs and files parallel to these. The main features of interest are:
- User machine
- User key pair: Public and private, which the client-side user has to create using ssh-keygen, creating files with names such as:
- ~/.ssh/id_rsa (private) and
- ~/.ssh/id_rsa.pub (public)
- In preparation, must be given to host's authorized_keys file
- ~/.ssh/known_hosts
- which receives the public key from the server, if user accepts it on first log in.
- Host (server) machine
- Host key pair: Public and Private
- are automatically created at some point like installation of openssh on the server. Typical names:
- /etc/ssh/ssh_host_rsa_key (private)
- /etc/ssh/ssh_host_rsa_key.pub (public)
- host offers the public key to the client-side user the first time the client-side user tries to connect with ssh. Client will store host's key in known_hosts
- ~/.ssh/authorized_keys
- In preparation, must be given the public key of each user who will log in.
- Sequence of events in an actual SSH (or rsync) session, showing how the files are involved.
(Note that there are two different common signature algorithms, RSA and DSA, so where this discussion uses 'rsa', the string 'dsa' could appear instead.)
Configuration/preparation
SSH connection and use
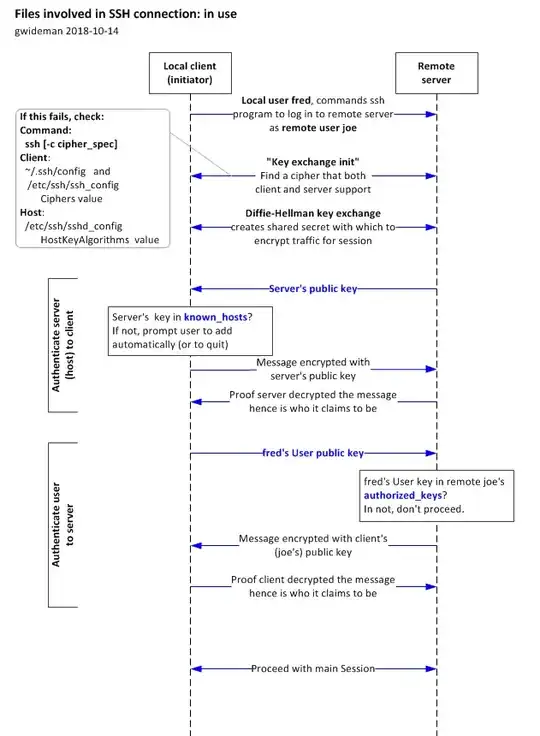
I hope these diagrams will be helpful.

