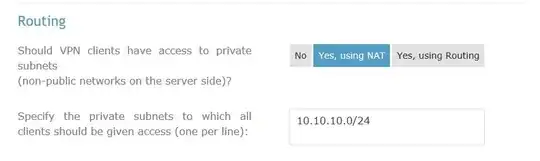
I have a server on the office lan with a public ip running open vpn. External vpn clients can connect to the vpn via the public ip.
But once connected they are unable to connect to other servers on the office lan, but they can access any site over wan.
My openvpn.conf is like
local xx.xx.xx.xx
port 8443
proto tcp
dev tun
ca ca.crt
cert server.crt
key server.key
dh dh2048.pem
server 10.8.0.0 255.255.255.0
;ifconfig-pool-persist ipp.txt
push "route 10.84.172.0 255.255.255.0"
push "redirect-gateway def1 bypass-dhcp"
push "dhcp-option DNS 10.84.172.117"
push "dhcp-option DNS 9.9.9.9"
duplicate-cn
keepalive 10 120
tls-auth ta.key 0
key-direction 0
cipher AES-128-CBC
auth SHA256
comp-lzo
max-clients 10
user nobody
group nogroup
persist-key
persist-tun
status openvpn-status.log
log openvpn.log
log-append openvpn.log
verb 9
client conf is so
client
dev tun
proto tcp
resolv-retry infinite
nobind
user nobody
group nogroup
persist-key
persist-tun
ca ca.crt
cert client.crt
key client.key
remote-cert-tls server
tls-auth ta.key 1
cipher AES-128-CBC
auth SHA256
key-direction 1
comp-lzo
verb 3
mute 20
ip route show output is
default via xx.xx.xx.xx dev ens19 onlink
10.8.0.0/24 via 10.8.0.2 dev tun0
10.8.0.2 dev tun0 proto kernel scope link src 10.8.0.1
10.84.172.0/24 dev ens18 proto kernel scope link src 10.84.172.76
xx.xx.xx.xx/27 dev ens19 proto kernel scope link src xx.xx.xx.xx
ifconfig output
ens18 Link encap:Ethernet HWaddr e2:d0:37:41:fe:62
inet addr:10.84.172.76 Bcast:10.84.172.255 Mask:255.255.255.0
inet6 addr: fe80::e0d0:37ff:fe41:fe62/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:300099 errors:0 dropped:7 overruns:0 frame:0
TX packets:813 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:45852701 (45.8 MB) TX bytes:108772 (108.7 KB)
ens19 Link encap:Ethernet HWaddr a2:c9:4f:0f:b3:a8
inet addr:xx.xx.xx.xx Bcast:xx.xx.xx.xx Mask:255.255.255.224
inet6 addr: fe80::a0c9:4fff:fe0f:b3a8/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:121480 errors:0 dropped:31009 overruns:0 frame:0
TX packets:37745 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:14195083 (14.1 MB) TX bytes:6904167 (6.9 MB)
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
inet6 addr: ::1/128 Scope:Host
UP LOOPBACK RUNNING MTU:65536 Metric:1
RX packets:176 errors:0 dropped:0 overruns:0 frame:0
TX packets:176 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1
RX bytes:13296 (13.2 KB) TX bytes:13296 (13.2 KB)
tun0 Link encap:UNSPEC HWaddr 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00
inet addr:10.8.0.1 P-t-P:10.8.0.2 Mask:255.255.255.255
UP POINTOPOINT RUNNING NOARP MULTICAST MTU:1500 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:0 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:100
RX bytes:0 (0.0 B) TX bytes:0 (0.0 B)
netsat -r output https://pastebin.com/30ZRNRri
ipv4 forwarding has been enabled
I believe i'm missing some static routes between the openvpn tun subnet and my actual local subnet but nothing im trying to route between them is working.