I have some AWS Cloudfront distributions spread out across different AWS accounts.
I have some AWS Cloudfront distributions spread out across different AWS accounts.
I'd like to store the access logs from these distributions in a single S3 bucket in a single AWS account.
This is possible, but it isn't documented (that I can find).
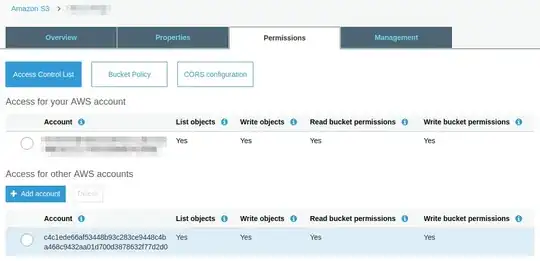
It isn't clear what update to the ACL is required on the log bucket, or what (if any) bucket policy is required.
What I seem to need is to update the ACL on the bucket to give FULL_CONTROL to a canonical id of what ever account in the other AWS account that Cloudfront uses to write logs.
If anyone else has configured this and can help, I'd be much obliged.