I have bastion host. I connect to the bastion host using username/password. And I have private key for destination Server. Flow:
Local Machine -> Bastion -> Destination
I know that It's dangerous to use Agent forwarding because someone may read my socket file (If they have root access to bastion host) while my session is open and access the destination server - so I should use ProxyCommand!
Now I'm just testing how to access destination server without private key if I have access to the bastion server - how dangerous is Agent forwarding.
Host bast
Hostname X.X.X.X
ForwardAgent yes
User bastion
Questions:
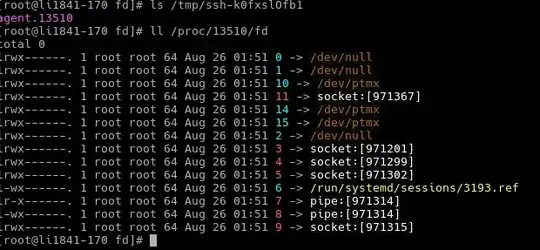
I've seen that there is information about the active agent to the following location in the bastion server: Ex: /tmp/ssh-{name}/agent.[PID]. I have root access but I can't read this file. I think only process Id is enough for this file, is not it?
if agent forwarding is enabled where can I find the socket file? I try to find at /proc/pid/fd/ location, where I saw several socket files.
how can I access to the destination server using the socket file? (How to access destination server via the ssh using socket file)
It tried to find socket files here:
/proc/PID/fd/
And then just try this command for each socket 3,4,5,9,11:
ssh -p 2072 -o "ProxyCommand socat - UNIX-CLIENT:/proc/PID/fd/11" app@[DESTINATION_HOST_URL]
Result:
2018/08/26 01:53:31 socat[13552] E connect(5, AF=1 "/proc/13510/fd/11", 19): Connection refused
ssh_exchange_identification: Connection closed by remote host
Log:
OpenSSH_7.4p1, OpenSSL 1.0.2k-fips 26 Jan 2017
debug1: Reading configuration data /etc/ssh/ssh_config
debug1: /etc/ssh/ssh_config line 58: Applying options for *
debug1: Executing proxy command: exec socat - UNIX-CLIENT:/proc/14003/fd/11
debug1: permanently_set_uid: 0/0
debug1: key_load_public: No such file or directory
debug1: identity file /root/.ssh/id_rsa type -1
debug1: key_load_public: No such file or directory
debug1: identity file /root/.ssh/id_rsa-cert type -1
debug1: key_load_public: No such file or directory
debug1: identity file /root/.ssh/id_dsa type -1
debug1: key_load_public: No such file or directory
debug1: identity file /root/.ssh/id_dsa-cert type -1
debug1: key_load_public: No such file or directory
debug1: identity file /root/.ssh/id_ecdsa type -1
debug1: key_load_public: No such file or directory
debug1: identity file /root/.ssh/id_ecdsa-cert type -1
debug1: key_load_public: No such file or directory
debug1: identity file /root/.ssh/id_ed25519 type -1
debug1: key_load_public: No such file or directory
debug1: identity file /root/.ssh/id_ed25519-cert type -1
debug1: Enabling compatibility mode for protocol 2.0
debug1: Local version string SSH-2.0-OpenSSH_7.4
debug1: permanently_drop_suid: 0
2018/08/26 03:10:17 socat[14073] E connect(5, AF=1 "/proc/14003/fd/11", 19): Connection refused
ssh_exchange_identification: Connection closed by remote host