HSTS doesn't try to handle mixed content at all: it just controls whether the browser should perform an internal 307 redirect to HTTPS whenever it tries to load HTTP URLs, or not. The mixed content warning is a feature of the browser, and all the current browsers do it (Mozilla Firefox 23+, Google Chrome 21+, Internet Explorer 10+, Edge from the beginning...). The mixed content warning blocks e.g. <script> and <iframe>, but not <img>.
The mixed content warning on all the browsers mentioned is checked before loading any content at all, i.e. before HSTS redirects, too. This seems only natural, and is also easy to test. By default, all external images are loaded even using plain HTTP, and a mixed content warning is given only for scripts and iframes.
HSTS only changes the situation where an image from an HSTS enabled domain is loaded using plain HTTP, and 307 Internal Redirect is performed. Worth noting: this is a situation with no mixed content warnings involved.
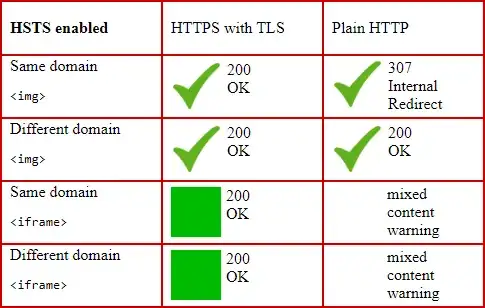
Therefore, HSTS does not work as a quick fix for the mixed content problem:
- You need to fix
http:// URLs on your site even for the domain itself.
- You need to ensure that you don't load external scripts from sources you don't trust.
- If the third party doesn't enable HSTS, it's still vulnerable to man-in-the-middle attacks.
- Third parties might load content from further external sources, and all this applies to those, too.
- The external content site might be cracked or do malicious activities by themselves.

