This depends on how the service is configured, more specifically on the Service SID Type.
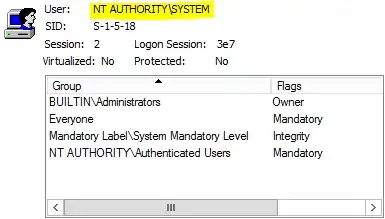
If the Service SID Type is "none" then the service just gets a plain SYSTEM token, the same as is used by other system processes such as services.exe and winlogon.exe and so on. This is the legacy situation; back in Windows XP all services had this sort of token, unless they were configured to run as a particular user account.
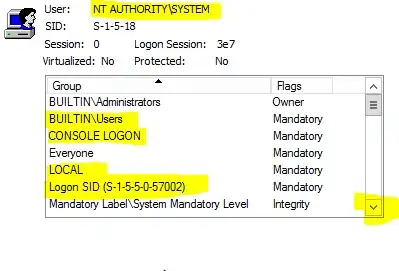
If the Service SID Type is "restricted" or "unrestricted" then a more specific token is generated for the service, including a special security identifier specific to that service, e.g., NT SERVICE\Schedule for the Task Scheduler. This helps to provide some granularity between different services. In Windows 7 and later most of the built-in services are "unrestricted". The Group Policy Service is an exception; this was probably an oversight on Microsoft's part. (I would have thought it was a deliberate choice for backwards compatibility, but this is undermined by the fact that in Windows 7 it always runs in a shared service process.)
As you have already observed, as well getting the NT SERVICE identifier, the token is given a number of other identifiers. This isn't documented as far as I can see but also isn't especially surprising; it makes the service token more like an interactive token would be, which can be useful. (It is particularly important that this be the case for restricted tokens, which would otherwise have very little access at all.)
As described in the self-answer, when multiple services are shared by a single process the process token has to contain every SID that any of the services needs. So if the Group Policy Service (or any other service with a SID type of "none") is sharing a process with an "unrestricted" service, it gets the exact same token as if it were itself "unrestricted".
Because earlier versions of Windows effectively ran the Group Policy Service as "unrestricted" and because even Windows 10 does so on machines with very limited memory, it would probably not be too dangerous to reconfigure the SID Type for the Group Policy service if it is absolutely necessary to do so. I don't recommend this other than perhaps as a very short-term solution, partly because there is still some risk (particularly regarding forwards compatibility) but mainly because every time you upgrade to a new version of Windows 10 the setting is likely to be reverted.
A better workaround would be for a startup script to run a scheduled task or to install and run a service to do whatever work is needed on the startup script's behalf.