I've managed to get strongswan running with eap-mschapv2 authentication using a server certificate. Now I want to try and use the eap-radius plugin with NPS running on a Windows 2012 R2 server to authenticate against Active Directory.
On the domain controller I created a new user, and group (VPN_USERS) for remote access.
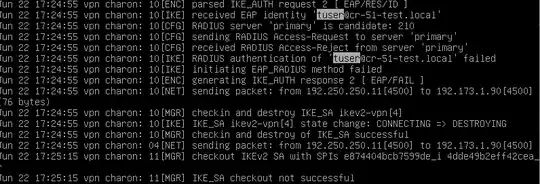
On the VPN server if I check out the syslog I see the following;
vpn charon: 08[IKE] received cert request for "C=US,O=CR-51 Test,CN=Root CA"
...
vpn charon: 09[CFG] selected peer config 'ikev2-vpn'
...
vpn charon: 09[IKE] authentication of 'vpn.cr-51-test.local' (myself) with pre-shared key
...
vpn charon: 09[ENC] generating IKE_AUTH response 1 [ IDr AUTH EAP/REQ/ID ]
...
vpn charon: 09[IKE] successfully created shared key MAC
....
vpn charon: 11[JOB] deleting half open IKE_SA after timeout
On a Windows 10 client get the following error during connection attempts:
dialed a connection named IKEv2 which has failed. The error code returned on failure is 13801.
On the NPS server in eventviewer there is an entry stating that the Network Policy Server denied access to a user and suggest changing the user's dial in settings in AD to allow access or to allow NPS to control access. It was originally set to allow NPS to control access and still fails when set to allow access.
Also I can not login with accounts on the domain controller other than a domain admin account after setting up NPS.
Heres the current configurations
ipsec.conf:
config setup
charondebug="ike 2, knl 2, cfg 2, net 2, esp 2, dmn 2, mgr 2"
uniqueids=no
conn ikev2-vpn
auto=add
compress=no
type=tunnel
keyexchange=ikev2
fragmentation=yes
forceencaps=yes
ike=aes256-sha1-modp1024,3des-sha1-modp1024!
esp=aes256-sha1,3des-sha1-modp1024!
dpdaction=clear
dpddelay=300s
rekey=no
left=%any
leftauth=pubkey
leftid=@vpn.cr-51-test.local
leftcert=/etc/ipsec.d/certs/vpn.cr-51-test.local.crt.pem
leftsendcert=always
leftsubnet=0.0.0.0/0
lefthostaccess=yes
leftfirewall=yes
right=%any
rightid=%any
rightauth=eap-radius
rightgroups="CN=VPN_USERS/CN=Users"
rightsourceip=10.10.0.0/24
rightdns=192.150.150.10
rightsendcert=never
rightfirewall=yes
eap_identity=%identity
/etc/strongswan.d/charon/eap-radius.conf:
(Just the sections I've modified)
load = yes
...
secret = testpass
server = 192.150.150.20
ipsec.secrets:
vpn : RSA "/path/to/key"
: PSK "testpass"
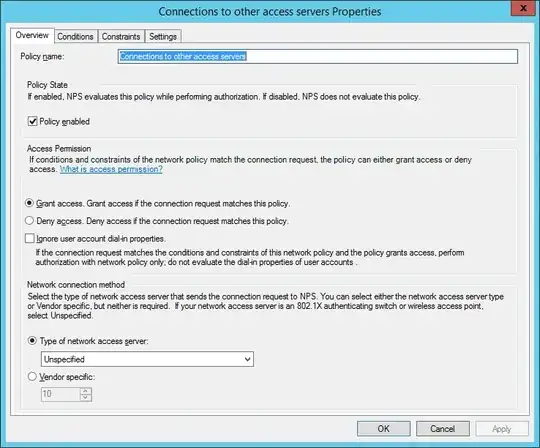
NPS configuration:
The NPS server is registered to the domain.
Freindly name: vpn
Addresss (IP or DNS): 192.150.150.11
Shared secret: testpass
Connection Request Policy
Type of network access server: Remote Access Server(VPN-Dialup)
Conditions:
NAS Port Type: VPN
Client Friendly Name: vpn
Network Access Policy
Type of network access server: vpn
Conditions:
NAS Port Type: VPN
Client Friendly Name: vpn
User Groups: VPN_USERS
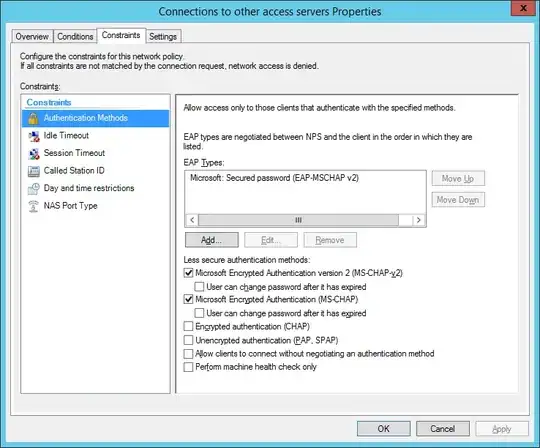
Constraints:
Authentication Methods: EAP-MSCHAP v2
NAS Port Type: VPN
Update
NPS Error
Log Name: Security Source: Microsoft-Windows-Security-Auditing Date: 6/22/2018 5:25:02 PM Event ID: 6273 Task Category: Network Policy Server Level: Information Keywords: Audit Failure User: N/A Computer: nps.cr-51-test.local Description: Network Policy Server denied access to a user.
Contact the Network Policy Server administrator for more information.
User: Security ID: CR-51-TEST\tuser Account Name: tuser@cr-51-test.local Account Domain: CR-51-TEST Fully Qualified Account Name: CR-51-TEST\tuser
Client Machine: Security ID: NULL SID Account Name: - Fully Qualified Account Name: - OS-Version: - Called Station Identifier: 192.250.250.11[4500] Calling Station Identifier: 192.173.1.90[4500]
NAS: NAS IPv4 Address: 192.250.250.11 NAS IPv6 Address: - NAS Identifier: strongSwan NAS Port-Type: Virtual NAS Port: 4
RADIUS Client: Client Friendly Name: vpn Client IP Address: 192.250.250.11
Authentication Details: Connection Request Policy Name: Use Windows authentication for all users Network Policy Name: - Authentication Provider: Windows Authentication Server: nps.cr-51-test.local Authentication Type: EAP EAP Type: - Account Session Identifier: - Logging Results: Accounting information was written to the local log file. Reason Code: 48 Reason: The connection request did not match any configured network policy.
Event Xml: 6273 1 0 12552 0 0x8010000000000000 531 Security nps.cr-51-test.local S-1-5-21-2365315230-2476318153-1929964036-1111 tuser@cr-51-test.local CR-51-TEST CR-51-TEST\tuser S-1-0-0 - - - 192.250.250.11[4500] 192.173.1.90[4500] 192.250.250.11 - strongSwan Virtual 4 vpn 192.250.250.11 Use Windows authentication for all users - Windows nps.cr-51-test.local EAP - - 48 The connection request did not match any configured network policy. Accounting information was written to the local log file.