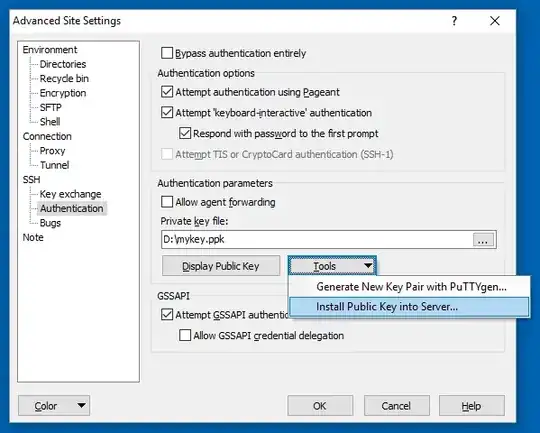
I created a public and private key using PuTTYgen and copied the public key to .ssh/authorized_keys under my user account.
Then I try to specify the private key when trying to log in, but apparently it doesn't pick it up and keep asking for the username/password I originally had. I'm using WinSCP to connect and specify the private key in Advanced/Authentication section. Am I missing any steps in WinSCP?
The content of authorized_keys looks like as below
ssh-rsa AAAAB3NzaC1yc2EAAAABpEVSiiRXi7tOHpkOyFa9w2OLpBep31k9lePCK7RQxsdfs9u11+rdu0XCidRKOY5j4anD1eDaNBj87wqZbsreRe5cFcsakyGUAYXAvqgGApvsep31k9lePCK7RQxlOY5j4anD1eDaNBj8LJO++K3SkUN8E0srRBO8YyMT6Y03/F7+AAAAB3NzaC1yc2Q4h2RLGtr12CDKSBVAnFEc+JucuF4uF0WY4Sh66MSFI63mCQFu9iYNYwWyT6lUo6sks4WypEVSiiRXi7tOHpkOyFa9w2OLpBzAlTA/VSQwdNTFYUI1vquaufZ9ORzTa6dkbBRo/mLVdevYSRMSDw1BUcinYz/ogdxRvw==
I changes the permission to .ssh to 700 and authorized_keys to 600.
Although I go to authentication section in WinSCP and specify the private key (as shown in the screenshot) it looks like it still need username and password and doesn't pick it up.
When I use PuTTY and specify the private key, after entering the login username it says
Server refused our key
Here is the log from PuTTY
2018-04-28 17:43:05 Connecting to 158.85.98.202 port 22
2018-04-28 17:43:05 We claim version: SSH-2.0-PuTTY_Release_0.70
2018-04-28 17:43:05 Server version: SSH-2.0-OpenSSH_7.4
2018-04-28 17:43:05 Using SSH protocol version 2
2018-04-28 17:43:05 Doing ECDH key exchange with curve Curve25519 and hash SHA-256
2018-04-28 17:43:05 Server also has ecdsa-sha2-nistp256 host key, but we don't know it
2018-04-28 17:43:05 Host key fingerprint is:
2018-04-28 17:43:05 ssh-ed25519 256 6b:0d:e2:f6:c5:9e:15:84:0c:1b:2c:19:62:cd:5b:ef
2018-04-28 17:43:05 Initialised AES-256 SDCTR client->server encryption
2018-04-28 17:43:05 Initialised HMAC-SHA-256 client->server MAC algorithm
2018-04-28 17:43:05 Initialised AES-256 SDCTR server->client encryption
2018-04-28 17:43:05 Initialised HMAC-SHA-256 server->client MAC algorithm
2018-04-28 17:43:05 Reading key file "C:\Users\\Desktop\private_key.ppk"
2018-04-28 17:43:09 Offered public key
2018-04-28 17:43:09 Server refused our key
2018-04-28 17:43:09 Using SSPI from SECUR32.DLL
2018-04-28 17:43:09 Attempting GSSAPI authentication
2018-04-28 17:43:09 GSSAPI authentication request refused