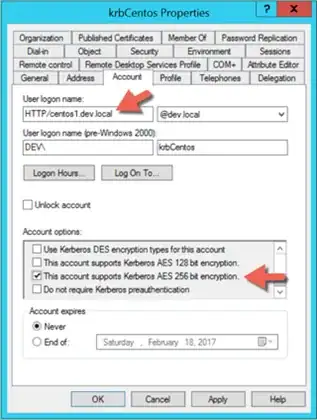
So my question has been explained from the title. I'd like to know how to detect whether a user is using keytab or password for authentication to Domain Controllers. I'm thinking about checking for log file to see what session has been used and if possible I'm not sure it will tell me something specific to distinguish them?
Update 1:
I'm thinking about checking for log file to see what session has been used and if possible I'm not sure it will tell me something specific to distinguish them?
this is not yet investigated