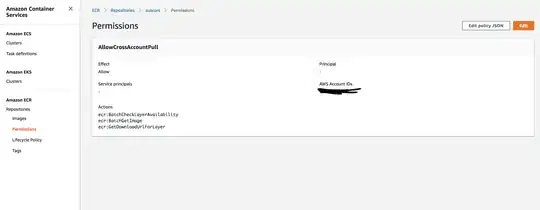
We have two AWS accounts. Account A has ECR repositories and Account B is meant to be able to pull from them.
I have tried setting the repository permission statements in Account A to allow pulling from Account B but AWS claims my policy is not valid.
I have tried:
- Setting the principal to be the account number of Account B. This results in the error
Your permission statements have one or more invalid parameters. Invalid parameter at 'PolicyText' failed to satisfy constraint: 'Invalid repository policy provided' - Setting the principal to the ARN of the root user in Account B (
arn:aws:iam::1234567891011:root). This results in the errorThe service name arn:aws:iam::1234567891011:root is invalid. A valid service name format is [service].amazonaws.com. - Setting the principal to the ARN of an IAM user in Account B. Same error as above.
The above have been done through the AWS console which does not allow editing the JSON directly for ECR permissions. I have tried the CLI command aws ecr set-repository-policy with the above changes but the same errors were returned in the terminal.
Adding permissions for IAM users within the same account works just fine.
The actions I have tried to add under the policy are:
"Action": [
"ecr:BatchGetImage",
"ecr:GetDownloadUrlForLayer",
"ecr:GetRepositoryPolicy",
"ecr:ListImages",
"ecr:DescribeRepositories"
]
Any ideas what I might be doing wrong?