I am looking for a way of tailoring custom RBAC (granting access\creating role & assigning permissions) to specific Azure AD blade.
In fact, I want my end user with a custom role to be able to modify only certain settings in Azure AD blade.
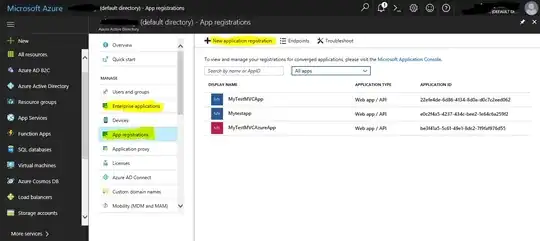
Here's the screenshot:
For example, I want the permissions to register an app (using App registration blade) and also permissions to manage this newly registered app via Enterprise applications blade.
The reason is that despite the Azure AD option "Users can register applications" (Azure AD – User Settings – App registrations – Users can register applications)
Even if you do allow users to register single-tenant LOB apps, there are limits to what can be registered. For example, developers who are not directory admins.
Users cannot make a single-tenant app a multi-tenant app.
When registering single-tenant LOB apps, users cannot request app-only permissions to other apps.
When registering single-tenant LOB apps, users cannot request delegated permissions to other apps if those permissions require admin consent.
Users cannot make changes to apps that they are not owners of. Source
According to resource provider enumeration, Microsoft.AzureActiveDirectory provider
is not a full ARM provider and does not provide any ARM operations.
so I cannot create a custom JSON template like:
Microsoft.AzureActiveDirectory/*/read
and import it via
New-AzureRmRoleDefinition
cmdlet.
The only possible actions with Microsoft.AzureActiveDirectory provider I've found are
- register the resource provider
- work with B2C directory.
In my case, B2B is used.