I have tried to execute(trigger) jenkins job (not a parameterized job) via curl command by using below methods but it showing these results. my jenkins version is Jenkins 2.73.3
curl -X POST -u jenkins_user_name:jenkins_user_passwd http://jenkins_server/job/job_name/build
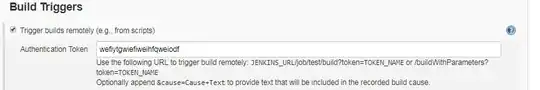
Therefore, I have created a Authentication Token for the Job

curl -X POST http://jenkins_server/job/job_name/build?token=wefiytgwiefiweihfqweiodf
It's also giving the same error. it says Forbidden 403
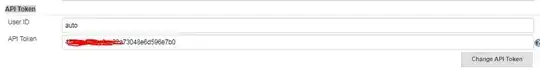
After that , I have created an API Token for jenkins User and tried.
curl -X POST -u auto:testingdae6dc22a73048e6d596e7b0 http://jenkins_server/job/job_name/build?token=wefiytgwiefiweihfqweiodf
But It also the same , it says Forbidden 403
Actually I have followed this answer as well. https://www.nczonline.net/blog/2015/10/triggering-jenkins-builds-by-url/ this is also not worked for me.
every time , It's 403 forbidden. I think I couldn't authenticate jenkins user properly.
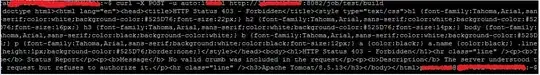
HTTP ERROR 403
Problem accessing /job/hailo_ci_pull_request/build. Reason:
Powered by Jetty:// 9.4.z-SNAPSHOT
` – CIsForCookies Feb 04 '19 at 13:58