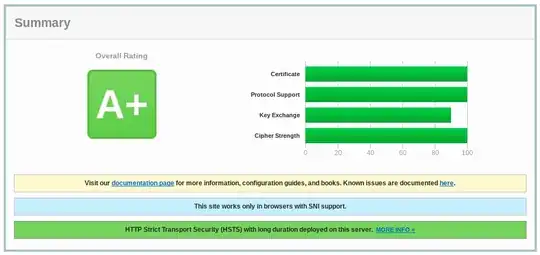
As of 2017-10, if you are using Diffie-Hellman, you ought to have both DH parameters and keys with equivalent 4096 bits RSA.
You are offering atleast one certificate for a 2048 bit key. You are also having unusual metadata in that certificate, check that (the default snake-oil certificate for saying "i dont serve non-sni clients" generally only has the host name in Common Name)
Edit: You will not be penalized in the SSL Labs rating for certificates that you exclusively offer no non-SNI clients. You will also not penalized for weak-keyed certificates you provide as part of your certificate chain to a known root.
You will find the full documentation on the rating on the ssllabs github account.
For suites that rely on DHE or ECDHE key exchange, the strength of DH
parameters is taken into account when determining the strength of the
handshake as a whole. Many servers that support DHE use DH parameters
that provide 1024 bits of security. On such servers, the strength of
the key exchange will never go above 1024 bits, even if the private
key is stronger (usually 2048 bits).
The rating guide doesnt say, but i was able to confirm that you cannot get rating 100 if your server prefers secp256v1 (equivalent to 3k bits RSA) while offering ECDHE ciphers that could be using secp384v1 (equivalent to 7k bits RSA).
Chrome 57 / Win 7
R
RSA 4096 (SHA256)
TLS 1.2 > http/1.1
TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
ECDH secp256r1 FS
The Apache manual does list one option to force this (simply ordering the Curves parameter by strength appears to be insufficient)
Compatibility: Available in httpd 2.4.8 and later, if using OpenSSL 1.0.2 or later
SSLOpenSSLConfCmd ECDHParameters brainpoolP256r1
https://httpd.apache.org/docs/2.4/mod/mod_ssl.html#sslopensslconfcmd
If you name a curve here that can be considered equivalent to RSA >=4096 bits, ssl labs will be using that for your ECDHE ciphers - listing you the clients that can no longer succeed a handshake with your server because they do not support that curve.
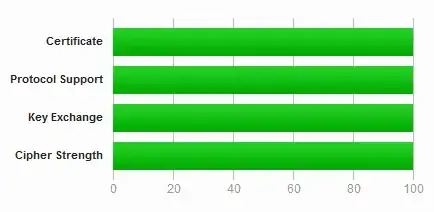
Carefully investigate the list of browsers you wish to support, choosing a non-standard EC curve will make your site inaccessible by many older browsers!