I need to have a health-check path for ALB setup that points to a server which has docker container Nginx. I do not have access inside the EC2 server to add a file there. I can just add something in Docker-Container
I have tried the following solution however it doesn't work for me because I have another block in my config file that prevents it I guess.
Nginx Solution for AWS Amazon ELB Health Checks - return 200 without IF
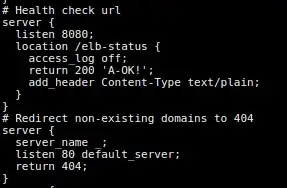
My config file looks like below:
server
{
listen 443 ssl http2;
server_name server-test.com;
access_log /var/log/nginx/nginx.access.log;
error_log /var/log/nginx/nginx.error.log;
ssl on;
ssl_certificate /etc/nginx/ssl/cert.pem;
ssl_certificate_key /etc/nginx/ssl/server.key;
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
ssl_prefer_server_ciphers on;
ssl_ciphers 'ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA256';
ssl_session_timeout 1d;
ssl_session_cache builtin:1000 shared:SSL:10m;
ssl_session_tickets off;
location /
{
proxy_pass http://server-test.io:5015/;
proxy_redirect off;
##proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
client_max_body_size 10m;
client_body_buffer_size 128k;
proxy_connect_timeout 90;
proxy_send_timeout 90;
proxy_read_timeout 90;
proxy_buffer_size 4k;
proxy_buffers 4 32k;
proxy_busy_buffers_size 64k;
proxy_temp_file_write_size 64k;
}
}
...
...
...
# Health check url
server {
location /elb-status {
access_log off;
return 200 'A-OK!';
add_header Content-Type text/plain;
}
}
# Redirect non-existing domains to 404
server {
server_name _;
listen 80 default_server;
return 404;
}
server {
server_name _;
listen 443 ssl;
ssl_certificate /etc/nginx/ssl/cert.pem;
ssl_certificate_key /etc/nginx/ssl/server.key;
return 404;
}
When I open the server with path /elb-status, it gives me 404 Not Found. And also the status of server under LoadBalancer is unhealty. I think it's because of block: "Redirect non-existing domains" but I need to have that block as well.
Any help would be appreciated.
Edited based on Andy reply:
The Nginx container uses both ports 80 and 443, I've set up the Target group for the servers, which include Nginx docker container, based on these ports but still the servers health check is Unhealthy.
Is there something that I'm missing here?