Let's say I own example.com, that I install and configure dkim on my server (apt-get install opendkim opendkim-tools, etc.), and that I add the relevant public key to the domain's DNS records.
Then when sending email from my server (example: with PHP mail(...) or postfix), it will have DKIM signature.
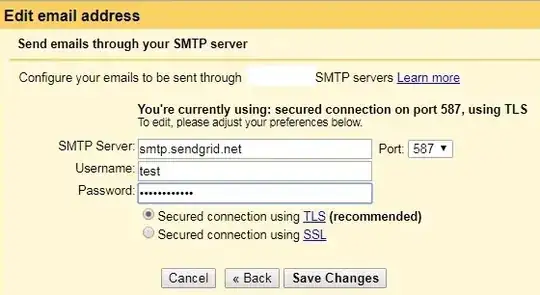
But I also send emails for contact@example.com from Gmail, using "Send mail as" feature with a Sendgrid SMTP.
But I don't see in Gmail the setting for DKIM. Will the mails sent from Gmail be banned / not sent correctly because they're not sent with DKIM signature?
How to send email from Gmail for my domain using DKIM? (using Send mail as feature)
Note: this is the "Send mail as" feature I'm speaking about: