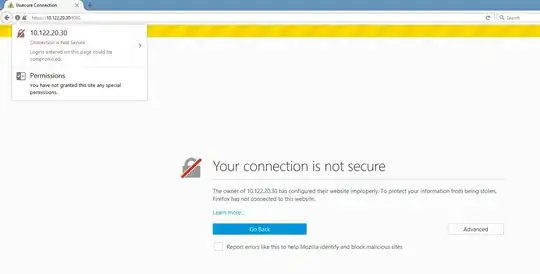
I have followed the information given in the goDaddy web-site to get the SSL certificate and installing it but Not successful.
I created the keystore:
keytool -keysize 2048 -genkey -alias tomcat -keyalg RSA -keystore D:\certificates\tomcat.keystore
generated the CSR:
keytool -certreq -keyalg RSA -alias tomcat -file D:\certificates\bimacsr.csr -keystore D:\certificates\tomcat.keystore
And after uploading the CSR in the goDaddy site, the certificates downloaded in a zip file which contains below 3 files-
gd_bundle-g2-g1.crtgdig2.crt.pem1c1f16606d7eadb7.crt
And after that used below 3 lines to install and import the certificate to keystore:
keytool -import -alias root -keystore D:\certificates\tomcat.keystore -trustcacerts -file D:\certificates\gd_bundle-g2-g1.crtkeytool -import -alias intermed -keystore D:\certificates\tomcat.keystore -trustcacerts -file D:\certificates\gdig2.crt.pemkeytool -import -alias tomcat -keystore D:\certificates\tomcat.keystore -trustcacerts -file D:\certificates\1c1f16606d7eadb7.crt
Finally made below changes in the server.xml file of conf/ tomcat 6 and 7
<Connector port="8443"
protocol="org.apache.coyote.http11.Http11Protocol"
maxHttpHeaderSize="8192"
maxThreads="150"
minSpareThreads="25"
maxSpareThreads="75"
enableLookups="false"
disableUploadTimeout="true"
acceptCount="100"
scheme="https"
secure="true"
SSLEnabled="true"
clientAuth="false"
sslProtocol="TLS"
keystoreFile="D:\certificates\tomcat.keystore"
keystorePass="mypwd"
/>
But when we access this in the browser getting "Not secured" in the left hand side
https://localhost:8443/
https://< public domain name>:8443/
Please take a look in the above explanation and suggest and help if i am missing any step or doing anything wrongly.