Pci DSS compliance stated that by June 2016 TLSv1.0 must be disabled. My cursory search taught me that a -TLSv1 in the SSLProtocals portion of the apache config would care for it (right next to the -SSLv3). I have tried each of the following lines in my /etc/apache2/conf_available/https.conf, but to no avail. I cannot figure out why changing these protocols makes no difference on my server (Apache/2.4.25 on Ubuntu 16.04)
SSLProtocol -all -SSLv3 -TLSv1 +TLSv1.1 +TLSv1.2
SSLProtocol -all +TLSv1.2
SSLProtocol +TLSv1.1 +TLSv1.2
SSLProtocol -TLSv1 +TLSv1.1 +TLSv1.2
Everytime I test with https://www.ssllabs.com/ssltest/index.html, I get the same result - TLSv1 is never turned off. What am I missing here? Are the TLS versions dependent on each other?
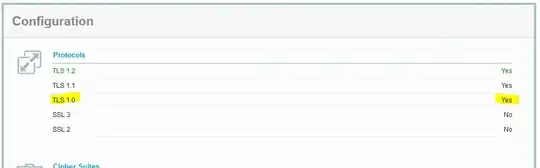
Promising Links that did not work for me
http://utdream.org/post.cfm/how-to-disable-tlsv1-0-for-pci-compliance-in-apache-2-2
https://ubuntuforums.org/showthread.php?t=2288000