How can I check whether port 5060 is open in centos? How can I test if my linux has real a real IP address and I set no iptables blocking rules or is there any tools which I can run in my linux so my internet provider's IP or gateway is able to listen or send with port 5060?
-
**Just an FYI**: given the OP is asking about port 5060, I would tend to think that he's asking about checking for the port used for the SIP protocol. SIP is what's used by most VoIP, port 5060 being the default. Assuming he's asking about SIP the checking would need to be looking for UDP **NOT** TCP. – slm Mar 05 '13 at 19:00
-
2This is an old thread, but SIP traffic [can very well be on TCP as well as UDP](https://tools.ietf.org/html/rfc2543#section-10). Not all servers will necessarily support both protocols, but some do. As mentioned, telnet will only test TCP connections. – GuitarPicker Apr 20 '15 at 16:20
9 Answers
nmap -v -sV localhost -p 5060
will tell you the truth.
You can also use:
netstat -apnt | grep 5060
or
ss -aln
- 346
- 1
- 7
lsof -i:5060 will not only show if it is open but what its actually doing.
Example:
root@root.com# lsof -i:5060
COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME
asterisk 1146 root 18u IPv4 0xffffff000a053c60 0t0 UDP *:sip
asterisk 1146 root 18u IPv4 0xffffff000a053c60 0t0 UDP *:sip
asterisk 1146 root 18u IPv4 0xffffff000a053c60 0t0 UDP *:sip
If you're checking specifically for asterisk, asterisk -r and then sip show channels will show if its listening and or doing anything with items connected.
If you think iptables is mucking with your results turn it off for your initial test. service iptables stop
The other high voted nmap command is wrong, as it's a TCP scan. Use this instead:
sudo nmap -v -sU 12.34.56.78 -p 5060
- 53,385
- 32
- 133
- 208
- 1,096
- 1
- 10
- 12
Since you initially posted here ^^
Nmap is a great tool for scanning ports, however since you do have access to each endpoints, I would rather use netcat to troubleshoot this.
According Wikipedia, SIP listen on 5060 / 5061 (UDP or TCP). To verify what port is listening, you can use one of those commands on the SIP server:
- lsof -P -n -iTCP -sTCP:LISTEN,ESTABLISHED
- netstat -ant
- tcpview (tcpvcon)
Once you know which port is listening, you can use Netcat (ncat, socat, iperf) to verify if a firewall blocks the connection/port.
- Stop SIP Server, so the port become available for you to test/use
- Run: netcat -l [-u] 506[0-1]
- From the client: netcat SIP_Server_IP_FQDN [-u] 506[0-1]
- Type some random text on the an endpoint, if it appears on the other endpoint then the traffic is not blocked.
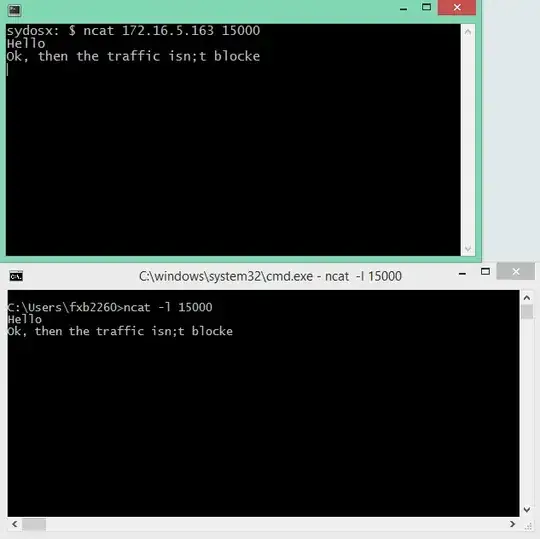
-u is for UDP, default is TCP
-l is for listening(server-mode), default is client-mode
- 334
- 2
- 10
Alternatively you can check it online via this site.
Just enter the IP address and port number.
- 53,385
- 32
- 133
- 208
- 11
- 1
-
2Probably not the best approuch. You need to have a web-facing server to use this. – Bart De Vos Sep 08 '11 at 09:33
If you have another machine running on the same network, try:
telnet <centos-machine-ip> 5060
If you're able to open a connection, then the port is open. You could also get yourself a copy of NMAP and port-scan your centos machine. If the ports are closed, check system-config-securitylevel and verify that your firewall is allowing connections.
I think you're also asking how to forward a port from your internet router to your centos machine (to host a web site from your house or something). If that's so, you'll need to figure out how to access your router, then forward a port from the router to your centos machine.
If it doesn't work, call your ISP and ask them how to do it. However, most ISPs block access to the common ports (most ISPs don't like people running web servers or mail servers from their house).
- 646
- 2
- 6
- 17
-
5telnet establishes TCP connection, SIP is a UDP protocal (UDP/5060) so you'll never be able to establish a telnet conection via telnet. – Zypher Nov 17 '09 at 22:36
-
You can check whether your port open, or not here, as well as check your IP.
netstat -nlp
Will show you open ports and applications, that use them.
- 53,385
- 32
- 133
- 208
- 1,077
- 3
- 14
- 25
If you only wish to see if the socket is bound you can use netstat or lsof to verify that the process owns the listening UDP and TCP sockets.
I would also suggest using a SIP testing tool like sipsak to test the higher level functionality.
Zypher: SIP is not UDP only.
from RFC 3162 page 141:
All SIP elements MUST implement UDP and TCP. SIP elements MAY
implement other protocols.
Making TCP mandatory for the UA is a substantial change from RFC
2543. It has arisen out of the need to handle larger messages,
which MUST use TCP, as discussed below. Thus, even if an element
never sends large messages, it may receive one and needs to be
able to handle them.
- 149
- 4
Probably a little high-level, but there are online tools to check port availability.
- 101