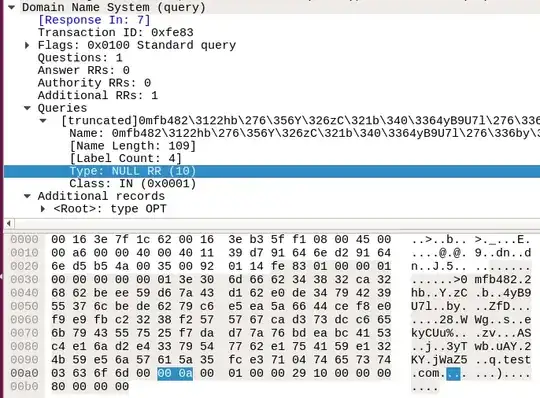
I am trying to detect DNS requests of type NULL using Snort. I located the type field of the request packet using Wireshark:
I found the following rule on McAfee:
alert udp any any -> any 53 (msg:"NULL request"; content:"|01 00|"; offset:2; within :4; content:"|00 00 0a 00 01|"; offset:12; within:255; threshold: type threshold, track by_src, count 10, seconds 5; sid: 5700001; rev: 1)
However, first of all this rule does not work for me as it throws the following error message:
ERROR: /etc/snort/rules/local.rules(7) within can't be used with itself, protected, offset, or depth
Which is odd, because apparently using within in combination with itself, protected, ... wasn't a problem for McAfee. I am using Snort version 2.9.9.0.
Furthermore, I also hoped that there would be a better way to address the type field of the DNS request. Instead of using a fixed offset to specify where in the packet you are looking for a specific pattern. Isn't there a way to look for the Type field in the Queries field of the Domain Name System section. This would also make the rule a lot more readable than using offsets and hexcode patterns.
So, my question is: Does anyone know a Snort rule that detects DNS requests of type NULL?