There are a lot of fine answers here, but they did not work for me or were actually overkill. The following suggestions were tested on Ubuntu 16.04 Apache 2.
A key observation is that the first virtual host on that port dictates the setting... even if its configuration doesn't explicitly specify a SSLProtocol value.
To determine the first virtual host:
bash
source /etc/apache2/envvars
apache2 -t -D DUMP_VHOSTS
exit
On CentOS, only one line will probably be needed:
httpd -t -D DUMP_VHOSTS
When you do this you should see a list of the virtual hosts and it might include a 443 section something like
*:443 is a NameVirtualHost
default server example.com (/etc/apache2/sites-enabled/example.com-le-ssl.conf:2)
port 443 namevhost sample.com (/etc/apache2/sites-enabled/sample.com-le-ssl.conf:2)
port 443 namevhost another.org (/etc/apache2/sites-enabled/another.org-le-ssl.conf:2)
port 443 namevhost lucky.com (/etc/apache2/sites-enabled/lucky.com-le-ssl.conf:2)
alias test15a.zzzzpost.com
When you see this, you might find that it's sufficient to update the SSLProtocol config for just that "default server" virtual host.
Another complication that you might run in to with earlier suggestions is that if you grep for occurrences of SSLProtocol in your /etc/apache2/ or /etc/httpd/ tree, you will not find configuration in other parts of your file system. This can be important if your configuration has Include directives. For example, if you've used the Let's Encrypt installer, it often adds these:
<IfModule mod_ssl.c>
<VirtualHost *:443>
ServerName mydomain.com
...
Include /etc/letsencrypt/options-ssl-apache.conf
...
</VirtualHost>
So my suggestions are:
1. Determine the first virtual host on the given port. See my example above
for details.
2. Inspect the configuration for that virtual host carefully.
a. If you find that config file explicitly sets SSLProtocol, make your change there.
b. If not, but you find it includes a config file that is setting SSLProtocol,
consider setting it there.
c. Otherwise, it's likely that setting it in your ssl.conf file would work.
d. If not, consider creating your own config file with your SSLProtocol setting
and including it in this first virtual host config, and possibly all virtual
host configs.
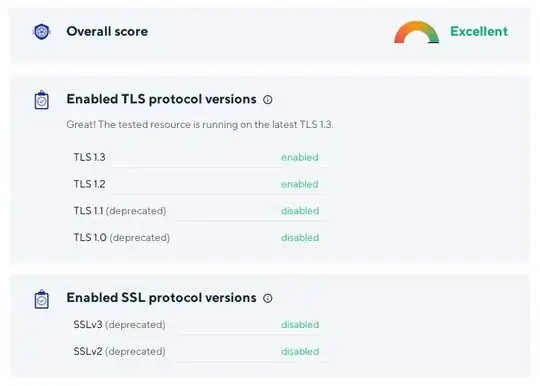
As mentioned by others, the configuration you want is
SSLProtocol TLSv1.2
After you make your change, you can quickly confirm it via:
systemctl reload apache2
# This ^^^ must be done before vvvv
nmap --script ssl-enum-ciphers -p 443 sample.com | grep TLSv
If you've been successful, this lists only TLSv1.2.