Communication between two EC2 instances relies on the ability of the traffic to be passed through:
- The Route Table
- The Network ACL
- The Security group (Associated with the instances)
- Any local Instance Firewall (e.g The windows firewall)
Unless it has been altered the Route Table should allow local traffic to flow locally so that shouldn't be a problem unless it has been altered.
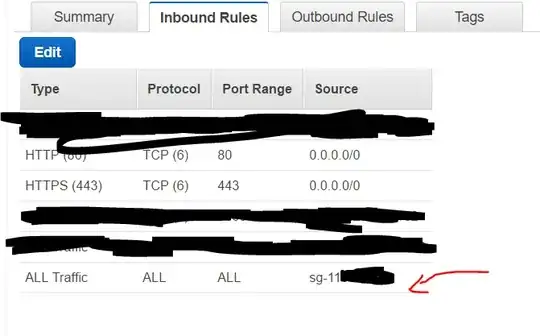
The Network ACL should also allow all traffic inbound and outbound unless it has been altered. Is the screen shot in your question from your Network ACL? I ask that because when I look at my Security groups they don't have a summary tab but my Network ACLs do. Make sure the Network ACL allows the traffic you want to test between the EC2 instance in both the inbound and outbound directions.
The Security group is stateful so all you need to do is allow the traffic you want Inbound. check the Security group and add the relevant Inbound rule.
Finally check the Host Based firewall. Even if the Route Table, the NACL and the Security group allow the correct traffic, the host needs to allow the traffic as well. If the instances are Microsoft instances you can adjust the basic firewall to allow the traffic.
Check the four features listed, one of them is stopping the traffic.