I just installed the latest Windows update (NSA vulnerability patch tuesday) and now I cannot connect to remote desktop.
- The server is remotely hosted. I don't have physical access. Server 2012 R1.
- Fortunately all web sites are running ok after reboot.
- I have not yet tried a second reboot because I'm a little scared to.
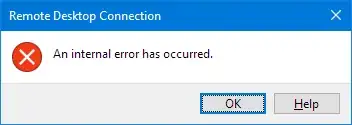
- When I try to connect I immediately get this message:
- "Remote Desktop Connection : An internal error has occured"
- Have tried from multiple clients. They all fail - including an iOS app which in addition gives me a 0x00000904 error.
- If I run
telnet servername 3389then it does initiate a connection, so I know the port is open. - I can connect just fine to other servers from my Win 10 (unpatched) machine.
- I cannot connect from my second laptop either, which is Win 10 Creators edition.
- Cannot find anything useful in Event Viewer.
- I've even tried wireshark which didn't show me anything useful.
- The best I have to diagnose is the ability to upload an ASPX page and run it.
I understand that the recent 'NSA edition' patch roundup had some RDP fixes - but I can't find anyone else who suddenly had issues hit week.
I want to have an idea what the problem is before I contact the hosting company, which is why I'm posting here.
Update:
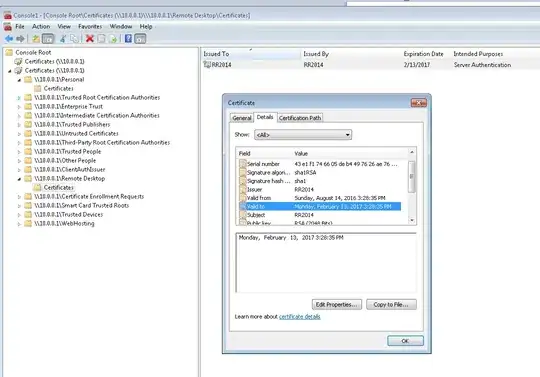
While I still don't have physical server access I remembered I have a Windows 7 VM hosted on the server itself. I was able to get into this and open the server certificates snap-in by connecting to the 10.0.0.1 local IP.
This is showing that the RDP certificate is indeed expired - although I get no errors when connecting that suggest as such. I certainly have been connecting daily and since it expired 2 months ago my guess is that some kind of security update removed whatever other certificate was in the Remote Desktop store and it did not renew itself.
So trying to figure out a way to install a different cert here now.
Update 2
Finally found this in the event log under 'Administrative Events' (by connecting remotely via the VM) :
"The Terminal Server has failed to create a new self signed certificate to be used for Terminal Server authentication on SSL connections. The relevant status code was Object already exists."
This seems helpful, albeit a slightly different error. Can't reboot tonight though so will have to check again tomorrow.