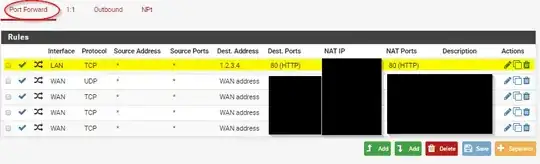
I have a PFSense box, with several hosts on its LAN. On the WAN side is a series of switches and routers. External hosts use a specific IP address (we'll call it 1.2.3.4) which is forwarded through several layers to the PFSense box, which then port forwards it to a host INSIDE the PFSense LAN network (let's call it 192.168.1.2).
On the distant network, everyone can use 1.2.3.4 to connect to that host and it all works fine. However, on the internal side, they have to remember to use a different address (192.168.1.2).
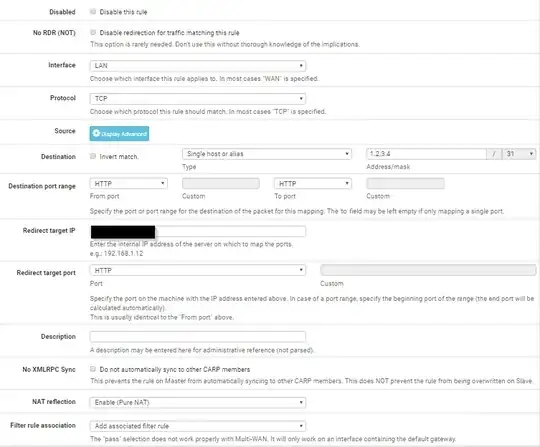
We want to have a way for the 1.2.3.4 address to work both outside AND inside the PFSense network. However, we do not want to change the internal 192.168.1.0/24 subnet. It's not as simple as NAT reflection, though, because the WAN address of the PFSense box is NOT 1.2.3.4 but rather an arbitrary IP assigned by the next layer. The 1.2.3.0/24 network is several routers away. I've tried multiple configurations of port forwarding, NAT, firewall rules, etc. all without success.
What I want to do is intercept all traffic bound for 1.2.3.4 at the PFSense router and have it sent to 192.168.1.2 instead. Bonus points if the traffic doesn't actually have to go through PFSense but is instead routed by the switch to avoid bandwidth bottlenecks (maybe some combination of DHCP/ARP could accomplish this).
Is this possible, and what's the best way to achieve it?
Diagram
┌──────────────────────┐ ╔══════════════════╗
│ Server (192.168.1.2) │ ║ Client 2 ║
└──────────────────────┘ ║ (Internal) ║
│ ║ Uses 192.168.1.2 ║
│ ║SHOULD use 1.2.3.4║
│ ╚══════════════════╝
│ │
├────────────────────────────────┘
│
┌──────────────────────┐
│ PFSense Router │
│ │
│ LAN: 192.168.1.1/24 │
│ WAN: 192.168.2.2 │
│ Virtual: 192.168.2.4 │
└──────────────────────┘
│
│
│
┌────────────────────┐
│ Router (NAT) │ This router transparently
│ │ converts incoming WAN traffic
│LAN: 192.168.2.1/24 │◀────── bound for 1.2.3.X to the
│ WAN: 1.2.3.1/24 │ equivalent 192.168.2.X address.
└────────────────────┘
│
│
│
╔══════════════╗
║ Client 1 ║
║ (External) ║
║ Uses 1.2.3.4 ║
╚══════════════╝
To clarify, for external clients, the sequence is as follows:
- Access 1.2.3.4
- NAT router converts to 192.168.2.4
- PFSense router receives traffic at 192.168.2.4 and maps internally to 192.168.1.2