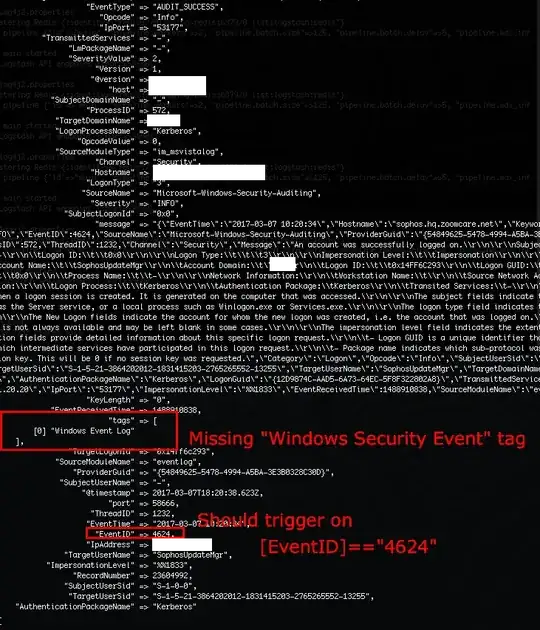
I've got nxlog on my Windows servers shipping logs to Logstash (JSON-formatted). I want to clone off the security events to a SIEM, so I added the logic to catch certain Windows Event IDs:
Even though the "Windows Event Log" tag gets applied (via "add_tag"), the "Windows Security Event" is never added, even when I review the logs and find an EventID like 4624.
For reference here's the full plain-text logstash.conf:
input {tcp{port=>1514}}
filter {
if "im_msvistalog" in [message] {
json {source => "message"}
mutate {add_tag => "Windows Event Log"}
if [EventID]=="4688" or [EventID]=="592" or [EventID]=="4624" or [EventID]=="528" or [EventID]=="540" or [EventID]=="5140" or [EventID]=="560" or [EventID]==5156 or [EventID]=="7045" or [EventID]=="601" or [EventID]=="4663" or [EventID]=="567" {
mutate {add_tag => "Windows Security Event"}
}
}
}
output {stdout{codec=>rubydebug}}