I'm trying to get a samba share working with correct IDs on Windows (SID) and Linux (uid/gid) clients. The problem is that the uids and gids are not properly mapped back to SIDs and SIDs are not resolved to names. What could lead to this problem and how can it be fixed?
What works
- mapping from Active Directory UNIX attributes to uid/gid on Linux
- access to the share
- Windows: UNC-Path in Explorer, Kerberos ticket is accepted (no question for credentials)
- Linux:
sudo mount -t cifs //ribonas2/test /mnt/ribonas2/smb/ -o domain=DOMAIN,username=paul.jaehne
- working with files on the share
What doesn't work
- files created on Windows have
Unix User\andUnix Group\(the UNIX uid and gid is also visible for a very short time when opening the security tab) instead ofDOMAIN\as prefix for users and groups - adding permissions is flawed: I can add principals from the domain and shortly afterwards the
DOMAIN\whateveris displayed correctly. When I wait for some time or look at the share from another computer then only the SID is displayed (the SID is correct, but not resolved to the name):
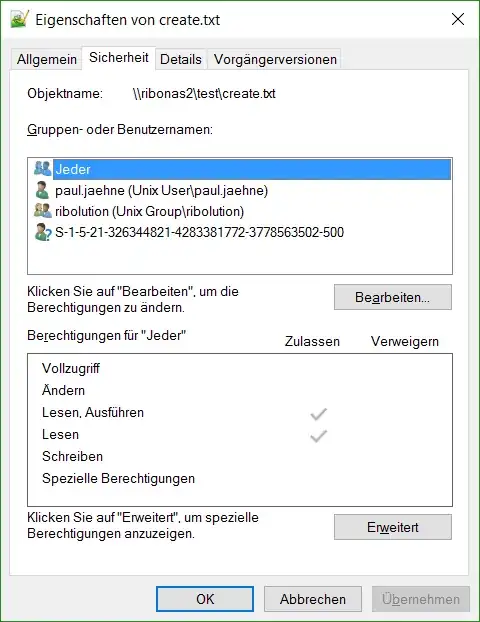
Environement/Configuration
- I used the following guides (can't add real links because of reputation requirements):
- multiple domain controllers (Windows Server 2003 and Windows Server 2012 R2)
- Active Directory schema from Windows Server 2003
- Ubuntu Server 16.04
- SSSD 1.13.4-1ubuntu1.1
- SMB 2:4.3.8+dfsg-0ubuntu1
- joined with both
realm joinandnet ads join
sssd.conf:
[sssd]
domains = domain.company.com
config_file_version = 2
services = nss, pam
[domain/domain.company.com]
realmd_tags = manages-system joined-with-adcli
ad_domain = domain.company.com
krb5_realm = DOMAIN.COMPANY.COM
id_provider = ad
cache_credentials = True
krb5_store_password_if_offline = True
enumerate = True
use_fully_qualified_names = False
fallback_homedir = /home/%d/%u
default_shell = /bin/bash
# use uid and gid from active directory
ldap_id_mapping = False
# needed to use correct active directory properties (Windows Server 2003)
ldap_schema = ad
ldap_user_object_class = person
ldap_user_name = msSFU30Name
ldap_user_uid_number = msSFU30UidNumber
ldap_user_gid_number = msSFU30GidNumber
ldap_user_home_directory = msSFU30HomeDirectory
ldap_user_shell = msSFU30LoginShell
ldap_user_gecos = displayName
ldap_group_object_class = group
ldap_group_name = msSFU30Name
ldap_group_gid_number = msSFU30GidNumber
smb.conf (settings from standard config file are indented):
[global]
server role = member server
workgroup = DOMAIN
realm = DOMAIN.COMPANY.COM
security = ads
password server = dc1.domain.company.com # shouldn't be necessary and same problem without this line
idmap config * : backend = tdb
idmap config * : range = 100000-999999
idmap config DOMAIN : backend = ad
idmap config DOMAIN : range = 10000-20000 # the UNIX attributes are manually assigned in this range
kerberos method = secrets and keytab
server string = %h server (Samba, Ubuntu)
dns proxy = no
log file = /var/log/samba/log.%m
log level = 10
max log size = 1000
syslog = 0
panic action = /usr/share/samba/panic-action %d
passdb backend = tdbsam
obey pam restrictions = yes
unix password sync = yes
passwd program = /usr/bin/passwd %u
passwd chat = *Enter\snew\s*\spassword:* %n\n *Retype\snew\s*\spassword:* %n\n *password\supdated\ssuccessfully* .
pam password change = yes
map to guest = bad user
usershare allow guests = yes
# needed for Windows ACL/ACE
vfs objects = acl_xattr
map acl inherit = yes
store dos attributes = yes
[test]
path = /srv/samba/test
writable = yes
TL;DR: Why aren't the UNIX attributes resolved to SIDs and why aren't the SIDs resolved to names?