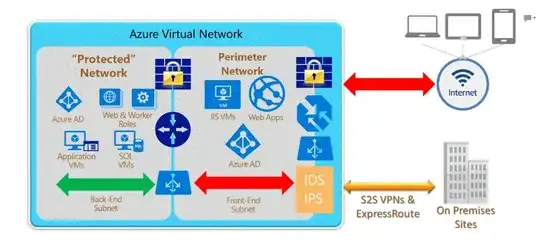
Just to start, I fully understand that a webserver should be on a seperate network, in the DMZ, not connected to the domain (or at least in a different forest). However, Im website developer and making this argument to networking.
I have made the argument that if someone was to gain control of the Web server, you wouldn't want a trust relationship to exists between said server and the DC. But I don't fully understand how to validate that this trust relationship would cause a problem.
In other words, how would one go about hacking an enterprise network by gaining access to an on-network web server and how do these principles change when talking about an azure VNET with a site to site VPN to the local network.