We have an app and the really long story short is that things have to be setup this way in order for the rest of the app not fail.
We have a domain
In IIS the 443 binding is setup to use a cert with:
CN=server02
When I hit the page for
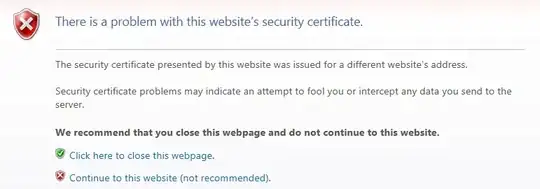
I get a SSL warning
I found this article
But would like to avoid the part about:
"Unfortunately, it'll also stop the browser from complaining about address mismatches on every other site you visit, as well. That's less than ideal, but it's the kind of tradeoff you get to make when you use IE."
I have also followed the steps outlined below however still give error
Fix 1 – Install the Certificate
Right-click the “Internet Explorer” icon, then choose “Run as administrator“.
Visit the website, and choose the option to “Continue to this website (not recommended).”.
Click where it says “Certificate error” in the address bar, then choose “View certificates“.
Select “Install Certificate…“.
Select “Next“.
Select the “Place all certificates in the following store” option.
Select “Browse…“.
Choose “Trusted Root Certification Authorities“, then select “OK“.
Select “Yes” when prompted with the security warning.
Select “OK” on the “The import was successful” message
Select “OK” on the “Certificate” box.
This is only for internal network
Is there anything I can add to IIS?
Is there anything I can add to DNS?
Any other work arounds?