i would like to auhenticate and authorize all users of one LDAP group (ApacheDS 2.0.0-20 on Windows, using multiple uniqueMember attributes in the group and the "Require ldap-group" statement in httpd config) for access to a web ressource.
The user which tries to authenticate is also part of this LDAP group and is authorized if i use the "Require valid-user" statement instead of "Require ldap-group" in httpd config.
Setup:
- Linux based Apache 2.4.23 (from OpenSuse 42.1 Apache Repository)
- LDAP: MS windows based ApacheDS 2.0.0-20
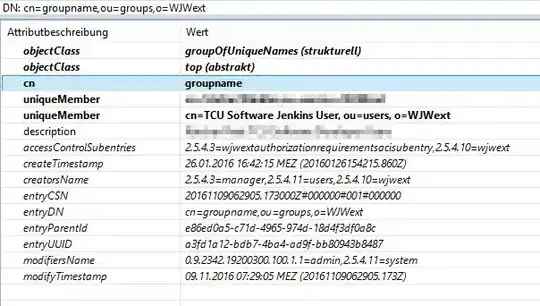
Group configuration in ApacheDS LDAP:
Excerpt of configuration of httpd:
<AuthnProviderAlias ldap ldapconfig>
LDAPReferrals Off
AuthLDAPBindDN "cn=query,ou=users,o=WJWext"
AuthLDAPBindPassword secretpassword
AuthLDAPURL "ldap://ldap.hostname:10389/o=WJWext?uid?sub"
</AuthnProviderAlias>
...
LogLevel trace7
<Location /xy>
...
AuthType Basic
AuthName "xy"
AuthBasicProvider ldapconfig
AuthLDAPGroupAttributeIsDN on
AuthLDAPGroupAttribute uniqueMember
AuthLDAPMaxSubGroupDepth 0
AuthLDAPSubGroupClass groupOfUniqueNames
Require ldap-group cn=groupname,ou=groups,o=WJWext
...
</Location>
The log file of httpd shows that the user can be authenticated but is not authorized by group:
[Tue Nov 08 21:44:23.601378 2016] [authz_core:debug] [pid 15148] mod_authz_core.c(809): [client a.b.c.d:59427] AH01626: authorization result of Require ldap-group cn=groupname,ou=groups,o=WJWext)
[Tue Nov 08 21:44:23.601415 2016] [authz_core:debug] [pid 15148] mod_authz_core.c(809): [client a.b.c.d:59427] AH01626: authorization result of <RequireAny>: denied (no authenticated user yet)
[Tue Nov 08 21:44:23.601547 2016] [authnz_ldap:debug] [pid 15148] mod_authnz_ldap.c(516): [client a.b.c.d:59427] AH01691: auth_ldap authenticate: using URL ldap://ldap.hostname:10389/o=WJWext?uid?sub
[Tue Nov 08 21:44:23.601590 2016] [authnz_ldap:trace1] [pid 15148] mod_authnz_ldap.c(537): [client a.b.c.d:59427] auth_ldap authenticate: final authn filter is (&(objectclass=*)(uid=hudson))
[Tue Nov 08 21:44:23.615090 2016] [ldap:trace5] [pid 15148] util_ldap.c(1843): [client a.b.c.d:59427] LDC 55e4b4a94070 used for authn, must be rebound
[Tue Nov 08 21:44:23.615236 2016] [authnz_ldap:debug] [pid 15148] mod_authnz_ldap.c(613): [client a.b.c.d:59427] AH01697: auth_ldap authenticate: accepting hudson
[Tue Nov 08 21:44:23.615410 2016] [authz_core:debug] [pid 15148] mod_authz_core.c(809): [client a.b.c.d:59427] AH01626: authorization result of Require ldap-group cn=groupname,ou=groups,o=WJWext:denied
What is somewhat surprising: In the log files and looking at a network traffic trace it seems that there's no search request for gathering the group membership of the user.
Is there any idea what we are doing wrong?